Forensic Implications of Windows Vista
Barrie Stewart
September 2007
i
Abstract
WindowsXPwaslaunchedin2001andhassincebeeninvolvedinmanydigital
investigations.Overthelastfewyears,forensicpractitionershavedevelopedathorough
understandingofthisoperatingsystemandarefullyawareofanychallengesitmaycreate
duringaninvestigation.Itssuccessor,WindowsVista,waslaunchedinJanuary2007andis
fastonitswaytobecomingtheplatformofchoicefornewPCs.Vistaintroducesmanynew
technologiesandrefinesanumberoffeaturescarriedoverfromXP.Thisreportfocuseson
someofthesetechnologiesand,inparticular,whateffecttheyhaveondigital
investigations.
Acknowledgements
ThanksgotoIanFergusonforarrangingtheplacementatQinetiQwherethemajorityof
thisresearchwasconducted.Also,thankstoPhilTurnerandthestaffatQinetiQfor
providingvaluablesupportandinsightduringthecourseoftheresearch.

ii
Table of Contents
Abstract .......................................................................................................... i
Acknowledgements .....................................................................................
i
Table of Contents .......................................................................................
ii
Chapter 1 - Introduction............................................................................
1
1.1 - Overview .................................................................................................................. 1
1.2 – Methods and Tools ................................................................................................ 1
1.3 – Existing Work ......................................................................................................... 2
Chapter 2 – User Account Control ..........................................................
4
2.1 – Introduction to User Account Conrol ............................................................... 4
2.2 – Standard User Accounts ....................................................................................... 4
2.3 – Administrator Accounts ....................................................................................... 5
2.4 – Effects of User Account Control ........................................................................ 6
iii
Chapter 3 – Changes to Windows Directory Structure ...................... 7
3.1 – Symbolic Links and Junctions ............................................................................ 7
3.2 – Directory Structure Changes .............................................................................. 8
3.2.1 – Parent Folder Junction ...................................................................................... 8
3.2.2 – User Data Legacy Folder Junctions ................................................................ 8
3.2.3 – Per-User Application Data Legacy Folder Junctions .................................. 8
3.2.4 – Per-Users OS Settings Legacy Folder Junctions .......................................... 9
3.2.5 – All Users Legacy Folder Symlink .................................................................. 10
3.2.6 – Default User Legacy Junction ........................................................................ 10
Chapter 4 – BitLocker ..............................................................................
11
4.1 – Introduction .......................................................................................................... 11
4.2 – BitLocker Requirements ..................................................................................... 12
4.3 – BitLocker Key Protectors .................................................................................. 13
4.3.1 – TPM-Only ............................................................................................................ 13
4.3.2 – USB Drive-Only ................................................................................................. 13
4.3.3 – TPM+PIN ............................................................................................................. 13
4.3.4 – TPM+USB ............................................................................................................ 14
4.4 – Boot Integrity Validation.................................................................................... 14
4.5 – BitLocker Encryption Algorithm ...................................................................... 15
iv
4.6 – BitLocker Keys .................................................................................................... 16
4.7 – Enabling BitLocker ............................................................................................... 17
4.8 – BitLocker Startup Keys ...................................................................................... 18
4.9 – BitLocker Recovery Passwords and Keys ...................................................... 19
4.10 – Identifying Presence of BitLocker ................................................................. 21
4.10.1 – Identification via BitLocker CLI .................................................................. 22
4.10.2 – Identification via BitLocker Control Panel ............................................... 23
4.10.3 – Identification via BitLocker Disk Management Snap-In ........................ 24
4.10.4 – Identification Using a Hex Editor ............................................................... 25
4.11 – Viewing BitLocker Recovery Passwords/Keys .......................................... 26
4.11.1 – Viewing Key Protectors via BitLocker CLI ............................................... 26
4.11.2 – Obtaining BitLocker Recovery Keys via BitLocker CLI ......................... 27
4.11.3 – Obtaining BitLocker Recovery Keys via BitLocker Control Panel ...... 28
4.11.4 – Other Sources of Recovery Keys ............................................................... 28
4.12 – Working with BitLocker Images ..................................................................... 29
4.12.1 – Unlocking via the BitLocker Control Panel .............................................. 29
4.12.2 – Unlocking via the BitLocker CLI ................................................................. 30
4.13 – Attacking BitLocker .......................................................................................... 32
Chapter 5 – Thumbnails ..........................................................................
33
5.1 – Thumbnails in Windows XP .............................................................................. 33
v
5.2 – Thumbnails in Windows Vista .......................................................................... 34
5.3 – Thumbcache File Format ................................................................................... 36
Chapter 6 – User File Activity in Vista ................................................
39
6.1 – Windows XP and Last Access Times .............................................................. 39
6.2 – Vista and Last Access Times ........................................................................... 39
6.3 – Recent Items Folder ........................................................................................... 39
6.4 – Recently Executed Programs ........................................................................... 40
6.5 – Vista RecentDocs Key ....................................................................................... 41
6.6 – The Windows Search Indexer .......................................................................... 42
6.7 – SuperFetch ............................................................................................................ 44
Chapter 7 – Backup Features in Vista ..................................................
46
7.1 – Restore Previous Versions ............................................................................... 46
7.2 – Other Vista Backup Options ............................................................................ 49
Chapter 8 – Windows Mail ......................................................................
50
8.1 – Windows Mail and Outlook Express .............................................................. 50
8.2 – Windows Mail Files and Folders ...................................................................... 50
8.2.1 – Account Property Data (.oeaccount) Files ................................................. 51
vi
8.2.2 – Mail Folders ...................................................................................................... 51
8.2.3 – Email (.eml) Files .............................................................................................. 51
8.3 – Windows Contacts .............................................................................................. 52
8.4 – Windows Mail Log File ....................................................................................... 52
8.5 – Newsgroups ......................................................................................................... 53
Chapter 9 – Internet Explorer 7 for Vista ...........................................
54
9.1 – Introductory Note ............................................................................................... 54
9.2 – Protected Mode for IE7 ....................................................................................... 54
9.3 – Internet Explorer 7 Cache and index.dat Files ............................................ 56
9.4 – Passwords ............................................................................................................. 58
9.4.1 – Internet Credentials ........................................................................................ 58
9.4.2 – AutoComplete Information ........................................................................... 59
9.5 – Deleting Browsing History ............................................................................... 61
Chapter 10 – Additional Points of Interest .........................................
62
10.1 – The Recycle Bin ................................................................................................ 62
10.2 – Acquisition of Physical Memory .................................................................. 63
10.3 – ReadyBoost ........................................................................................................ 63
10.4 – Transactional NTFS and Transactional Registry ...................................... 63
vii
10.5 – Disk Defragmenter ........................................................................................... 64
Chapter 11 – Conclusion .........................................................................
65
Chapter 12 – Suggestions for Further Work .......................................
67
Appendices
Appendix A – References ........................................................................................... 69
Appendix B – Features Comparison .......................................................................... 80
Appendix C – Registry Keys ....................................................................................... 85
Appendix D – The BitLocker Command-Line Interface ........................................ 91

‐1‐
Chapter 1
Introduction
ThereportattemptstoidentifythetechnologiesinWindowsVistawhichmayhavean
impactoncurrentdigitalforensicpracticesandprovideadetailedoverviewofeachone.In
additiontoprovidinganoverview,thereportalsoprovidesanypossiblesolutionstonew
problems and highlights any differences when compared to the investigation of legacy
Windowsplatforms.
1.1 – Overview
The report begins by discussing some of the methods and tools used to conduct the
research.ItthenoutlinessomeexistingresearchmaterialthatlooksatWindowsVistafrom
aforensicperspective.ThenextchapterexplainstheUserAccountControlfeatureand,in
particular,howitaffectsinvestigationsinaliveresponsescenario.Chapter3looksatone
ofthemorefundamentalchangesinVista–thechangestothebasic directory structure.
Chapter 4 details the BitLocker encryption system used in Vistawhilethenextchapter
discussesthechangestothethumbnailcache.Chapter6identifiestheproblemsintryingto
determineuserfileactivityandChapter7discussessomeofVista’snewbackupfeatures.
ThenexttwochaptersdiscussWindowsMailandInternetExplorer7respectively.Chapter
10listanumberoftechnologieswhich,whilestillimportant,didnotmerithavinganentire
chapter dedicated to them. The report then ends with the conclusionandoutlinessome
suggestionsforfuturework.AppendixB containsa comprehensivelist ofwhichfeatures
are available in the different editions of Vista. Appendix C lists a number of important
registrykeysthatcanbeusedduringaninvestigation.Thefinalappendixcontainsalistof
usefulcommandsforinvestigatorsdealingwithBitLocker.
1.2 – Methods and Tools
Themajorityoftheresearchforthisreportwasconductedonfourdifferentmachines:
‐2‐
• AnIntelPentiumIV2.8GHzPCwith1024MBDDRrunningVistaBusiness.
• AnIntelPentiumIV2.8GHzPCwith512MBDDRrunningVistaUltimate.
• AnAMDX244002x2.3GHzPCwith2048MBDDR‐IIrunningWindowsXPPro.
• AnIntelCore 2 Duo 1.66 GHz laptop with 1024 MB DDR‐IIrunning Vista Home
PremiumandUltimate.
The first machine was used to various features documented throughout the report. The
secondmachinewasusedforconductingexperimentswithBitLocker.Thethird machine
wasusedtorunvirtualmachinesandthelaptopwasusedasasourceofsomeofthetest
data used in the report. Unfortunately, a machine witha TPM discussedlaterwasnot
availablefortestingthesecurestartupfeaturesofBitLocker.
VMware Workstation v6 1 was used for creating virtual machinesVMswhichwere
usedthroughouttheresearch.ThisincludedVMsrunningWindowsXP,VistaHomeBasic,
VistaHomePremium,VistaBusiness,andVistaUltimate.
WinHex2andNotepad3wereusedthemajorityofthetimewhenexamininglogs
andundocumentedfiletypes.Process Monitor4andRegshot5were usedto monitor
registryandfileactivityforprocessesandFTKImager6wasusedforimagingdrives.
Themajorityoftestingwasconductedonphysicalmachinesandthenonvirtualmachines.
While this validated results, it was also useful as the VMs could then be restored to
snapshotstakenimmediatelyafterVistawasinstalled.
1.3 – Existing Work
AsVistaiscurrentlylessthanayearold,thereisnotagreatdealofdetailedinformation
currentlyavailable.“NotesonVistaForensics”isatwo‐partarticle78byJamieMorris,
founderofForensicFocus9.Thearticleprovidesagenerallookatsomeofthenew
features of Vista and their possible effects on forensic investigations. Lance Mueller of
Guidance Software 10 made a presentation 11 at CEIC2007 that provided a more
detailedlookatsomeofthepointsavailablein7and8.Morerecently,therehavebeena
number of Microsoft presentations 12 13 which have contained material on a broad
‐3‐
rangeofforensicissuesinVista.ChristopherHargreavesandHowardChiversofCranfield
Universityhavewrittenapaper14whichcoversmanyofthepracticalaspectsofdealing
withVistasystems.

‐4‐
Chapter 2
User Account Control
This chapter provides details of the User Account Control feature of Windows Vista and
howitcanaffectinvestigations.
2.1 – Introduction to User Account Control
OneofthemajorsecurityfeaturesintroducedwithVistaisUser Account Control UAC.
Microsoft’smaingoalwithUACisto“reducetheexposureandattack surface of the
operatingsystembyrequiringthatallusersruninstandardusermode”15.
Ithasbeen
introducedasamechanismtoreducethepossibilityofusersinadvertentlymakingchanges
to their system which may have adverse effects and also to reduceopportunitiesfor
malwaretobeintroducedtoasystem.
2.2 – Standard User Accounts
Vistausestwotypesofuseraccount:astandarduseraccountand an administrator
account.AspartoftheVistainstallationprocess,anadministrator account must be
created.Anyaccountsthataresubsequentlycreatedarestandarduseraccountsbydefault,
butthereisalsotheoptiontocreatethemasadministratoraccounts.AllaccountsinVista
work on the principle of least privilege whereby they are only allowed access to the
resourcesthatarenecessaryfortheirpurpose.Incomparisonto previous versions of
Windows, standard user accounts have been given additional privileges in order to
perform common tasks e.g. the ability to change the time zonebutforthemostpart
function in a similar fashion to Windows XP limited user accounts.Ifastandarduser
attemptstoperformanadministrativetask,theyaregreetedwiththeCredentialUIshown
inFigure2.1.Thisallowsthestandardusertobe“elevated”toadministratorlevelonlyif
thecorrectpasswordisprovidedandthetaskcanbecompleted.

‐5‐
Figure2.1‐CredentialUIfor ElevatingStandardUsers
2.3 – Administrator Accounts
InearlierversionsofWindows,anyprocessthatanadministratorranwouldautomatically
runwithadministrativeprivileges.Theproblemwiththisscenarioisthatanymalwarethat
was run by an administrator had the potential to make changes to the system without
havingtoexplicitlyaskforconfirmation.UACinVistaprotects against this by running
administratoraccountsinAdministratorApprovalMode.InAdministratorApprovalMode,
Vista runs most applications with standard user privileges eventhoughtheuserisan
administrator.Whentheuserattemptstoperformanactionthatrequiresadministrative
privileges,theyarepromptedbytheConsentUIbeforetheactioncanbecompletedsee
Figure2.2.
Figure2.2‐ConsentUIforelevatingadministrators
‐6‐
Vistamanagestoachievethisstandard/administratordualityfor administratoraccounts
bycreatingtwoaccesstokensforeachmemberoftheAdministratorgroup:onetoken
which has full administrative privilegesand a second “filtered” token with User Account
Protection16.Itisthisfilteredtokenthatisusedbydefaultinanadministratoraccount
withtheprivilegedtokenonlyeverbeingusedaftertheuserhasconsentedviatheConsent
UI.AusercanexplicitlytellUACtousetheprivilegedtokenbyright‐clickingonaprogram
and using the “Run as administrator”option.Thisisoftennecessaryevenwhen running
programs from an administrator account. For example, WinHex v14.3 refuses to open
physicaldiskunlesslaunchedusingthe“Runasadministrator”option.
Aninvestigatorcanquicklydeterminewhatcategoryauserfallsintoonalivemachineby
openingacommandpromptandusingthe
whoami /allcommand.Usersbelongingtothe
Administratorsgroupwillhavea
“BUILTIN\Administrators”entryundertheGroup
Informationsectionnote:theSIDfortheAdministratorsgroupisS‐1‐5‐32‐544.
2.4 – Effects of User Account Control
UAC is enabled by default and one of the major implications of it running is that many
legacyapplicationswerenotcompatiblewithstandarduseraccounts. Vista gets around
thisproblembyintroducingfilesystemandregistryvirtualization where writes to
protected file system and registrylocationsareinterceptedand written to safe, low
integritylocations.Itshouldbenotedthatsometoolswhichareessentialinaliveincident
responsemayrefusetorununderastandarduseraccountevenwhenusingvirtualization.
ItisalsofundamentaltothenewsecuritymodelintroducedinInternet Explorer 7 see
Chapter9andisalsoofsignificantwhenaninvestigatorapproachesamachinetheymay
suspectisrunningwithBitLockerencryptionseeChapter4fordetails.

‐7‐
Chapter 3
Changes to Windows Directory Structure
Thischapterdescribesthemethods used to create backwards‐compatibility with the XP
folderstructurewhileallowingVistatouseadirectorystructure of its own.The chapter
finishesbyprovidingalistoflegacyfoldersandtheirVistacounterpart.
3.1 – Symbolic Links and Junctions
ManyofthefoldersfamiliartoXPusershavebeenreplacedinVista.Inordertomaintain
backwards‐compatibility with legacy applications, Vista uses a combination of the new
NTFSsymboliclinksandtheolderNTFSjunctionpoints.Symboliclinks
symlinks
work
forbothfilesanddirectoriesinVista.Insteadofpointingdirectlytodata,symlinkscontain
asymbolicpaththattheOSusestoidentifythetargetfilefilesystem object. Symlinks
appeartransparentbecausewhenauserorapplicationattempttoopen,read,orwritetoa
symboliclink,theoperatingsystemredirectstheattemptedactiontothetargetobjectof
the symlinks. By default, symlinks in Vista allow users to create symlinks to file system
objectslocatedacrosslocalvolumesandarecreatedassoftlinks.
Vistaalsoprovidestheoptiontocreatehardsymlinks.Theycanonlybecreatedforfiles
and,unlikedefaultsymlinks,thetargetobjectmustresideonthesameNTFSvolumeasthe
symlink.TheycanbethoughtofasanN:1associationbetweenafilenameandafilesystem
dataobject17astheyusethesameMFTentryastheoriginalfile.Byaddinganewhard
link, a new name attribute is created in the MFT. In addition, the data object contains a
referencecountofhowmanyfilenamesrefertoit.Theobjectcanonlybedeletedifand
onlyiftherearenolongeranyfilenamesreferencingit.
JunctionpointsinNTFSaresimilartosymlinksexcepttheyare used exclusively for
directoriesandvolumes.

‐8‐
3.2 – Directory Structure Changes
The following tables based on tables available from 18 show lists of the directory
structurechangesinVistaandeachfolder’sXPcounterpart.Any time an application
attemptstowritetooneofthelegacylocations,Vistaautomaticallyredirectsthemtothe
newlocationspecifiedinthejunction/symlink.Forthecompletelistofdirectoryjunctions
inVistasee18.
3.2.1 – Parent Folder Junction
XPFolder VistaEquivalent Junction/Symlink
C:\Documents and Settings\ C:\Users\
Junction
3.2.2 – User Data Legacy Folder Junctions
XPFolder VistaEquivalent Junction/Symlink
C:\Documents and Settings\
<username>\My Documents\
C:\Users\<username>\
Documents
Junction
C:\Documents and Settings\
<username>\My Documents\My Music
C:\Users\<username>\
Music
Junction
C:\Documents and Settings\
<username>\ My Documents\
My Pictures
C:\Users\<username>\
Pictures
Junction
C:\Documents and Settings\
<username>\My Documents\
My Videos
C:\Users\<username>\
Videos
Junction
3.2.3 – Per-User Application Data Legacy Folder Junctions
XPFolder VistaEquivalent Junction/Symlink
C:\Documents and Settings\
<username>\Local Settings
C:\Users\<username>\
AppData\Local
Junction

‐9‐
XPFolder VistaEquivalent Junction/Symlink
C:\Documents and Settings\
<username>\Local Settings\
Application Data
C:\Users\<username>\
AppData\Local
Junction
C:\Documents and Settings\
<username>\Local Settings\
Temporary Internet Files
C:\Users\<username>\
AppData\Local\Microsoft\
Windows\Temporary Internet
Files
Junction
C:\Documents and Settings\
<username>\Local Settings\
History
C:\Users\<username>\
AppData\Local\Microsoft\
Windows\History
Junction
C:\Documents and Settings\
<username>\Application Data\
C:\Users\<username>\
AppData\Roaming
Junction
3.2.4 – Per-User OS Settings Legacy Folder Junctions
XPFolder VistaEquivalent Junction/Symlink
C:\Documents and Settings\
<username>\Cookies\
C:\Roaming\Microsoft\
Windows\Cookies
Junction
C:\Documents and Settings\
<username>\Recent\
C:\Roaming\Microsoft\
Windows\Recent
Junction
C:\Documents and Settings\
<username>\Nethood\
C:\Roaming\Microsoft\
Windows\Network Shortcuts
Junction
C:\Documents and Settings\
<username>\Printhood\
C:\Roaming\Microsoft\
Windows\Printer Shortcuts
Junction
C:\Documents and Settings\
<username>\SendTo\
C:\Roaming\Microsoft\
Windows\Send To
Junction
C:\Documents and Settings\
<username>\StartMenu
C:\Roaming\Microsoft\
Windows\StartMenu
Junction
C:\Documents and Settings\
<username>\Templates\
C:\Roaming\Microsoft\
Windows\Templates
Junction

‐10‐
3.2.5 – All Users Legacy Folder Symlink
XPFolder VistaEquivalent Junction/Symlink
C:\Users\All Users C:\ProgramData
Symlink
3.2.6 – Default User Legacy Junction
XPFolder VistaEquivalent Junction/Symlink
C:\Documents and Settings\
Default User
C:\Users\Default
Junction

‐11‐
Chapter 4
BitLocker
ThischapterdiscussestheBitLockerencryptiontechnologyintroducedinVista.Itstartsby
giving an introduction to BitLocker then provides details of the security features it
provides.The chapterthen describes someofthe practical challengeswhenfacedwith a
BitLockerencryptedsystemand,inparticular,theimportanceof dealing with BitLocker
systemsinaliveresponsescenario.
4.1 – Introduction
BitLockerisoneofthemosttalked about features available in Vista. Its fundamental
purposeistoprotectthedataonalaptoporPCevenifitisstolen.Datalosshasbeenthrust
intothepubliceyeoverthelastfewyearsduetoanumberofhighprofilecasesinvolving
lossofpersonaldata1920.ThenonprofitconsumerrightsorganizationPrivacyRights
Clearinghouse21listsinstancesofdatalosssinceJanuary2005whichcurrentlystandsat
a total of over 159 million data records of US residents being exposed. BitLocker is
available in the Ultimate and Enterprise editions of Vista and is aimed primarily at
commercial and governmentorganizationslooking tominimizethe risks associatedwith
dataloss.
WithpreviousversionsofWindows,accessingdataontheOSdrive was as simple as
removingthephysicaldrivefromthemachineandthenaccessingitasasecondarydriveon
another machine. This made it possible to access any data on the drive by using the
administrator privileges of the second machine. An even simpler solution was to use a
software‐basedattacktogainaccesstoanadministratoraccountonthemachine.This
couldbeachievedbybootingthecomputerfromaCDorUSBdrivecontainingtoolssuchas
Offline NT Password & Registry Editor 22 or ophcrack 23. BitLocker overcomes the
limitationsofitspredecessorsbyprovidingtwolayersofprotection:
‐12‐
• SecureStartup–Verifiestheintegrityofthepre‐OSbootcomponentsandprotects
againstofflineattacks
• Fullvolumeencryption–EncryptstheentireWindowsOSvolumeontheharddrive
everythingonthevolumeisencryptedincludinguserdata,systemfiles,fileslack,
unallocatedspaceetc.
TheaimofBitLockeristoprovidethisprotectioninaneasytouse mannerinwhichthe
encryption/decryptionprocessistransparenttotheuser,withminimaldiskandprocessor
overhead,andwithasimplerecoveryprocessintheeventofhardwarefailureorchanges.
4.2 – BitLocker Requirements
There are several hardware requirements that must be met in orderforBitLockertobe
enabled on a volume. The first requirements stem from BitLockerstoringitsencryption
key in a hardware device that is separate from the hard disk that is being encrypted.
Therefore,thefollowinghardwarecomponentsarenecessary:
• IftheuserwishestobenefitfromthesecurestartupcomponentofBitLocker,there
aretworequirements:
o A Trusted Platform Module TPM which is a tamper‐proof microchip that
canperformcertainsecurity‐relatedfunctions.TheTPMistypicallyinstalled
on the motherboard of the PC or laptop. BitLocker requires a version 1.2
TPMtofunction.
o ATrustedComputingGroupTGC‐compliantBIOS.
• IftheuserdoesnothaveaTPM orwishestousetheTPMStartupKeymode,
BitLockerrequiresthefollowingtostorethestartupkey:
o AremovableUSBdevicee.g.aUSBflashdrive
o AsystemBIOSthatsupportsreadingfromaUSBdeviceinthepre‐OS
environment
• Theharddrivemustbepartitionedwithatleasttwovolumes:
‐13‐
o AnNTFS‐formattedOSvolumewhichcontainstheVistaoperatingsystem
and all of its supporting components. This volume will be encrypted by
BitLocker.
o An NTFS‐formatted system volume at least 1.5GB in size which contains
thefilesnecessarytoboottheoperatingsystemaswellasbeingrequiredfor
OSupgrades.Thisvolumeisrequiredtoremainunencrypted.
4.3 – BitLocker Key Protectors
TherearefourdifferentauthenticationmodesthatcanbeusedwithBitLocker.Thechoice
of which authentication mode to use depends on the hardware availableandtheusers
intendedlevelofinvolvementinthebootprocess.
4.3.1 – TPM-Only
TheTPM‐onlymodeistheeasiesttouseofthefourauthentication modesasit doesnot
requireanyuserinteraction.TheTPMsimplychecksthepre‐OSbootcomponentsandthen
boots into Windows if the check has been successful. This protects against any software
attacksbutmaybesusceptibletospecializedhardwareattacks.
4.3.2 – USB Drive-Only
BitLockerprovidesprotectionintheabsenceofaTPMbyallowingtheusertostorea
startupkeyonaremovableUSBdrive.Inthisscenario,theusermustentertheUSBdrive
everytimetheywishtobootintoWindows.BitLockerverifiestheUSBdrivecontainsthe
startup key pre‐OS and will then boot into the operating system. This method also
protectsagainsthardwareattacksbutsuffersfromtheriskofthepre‐OSattacksortheUSB
drivebeinglostorstolen.Thereisalsotheriskofthestartupkeybeingcopiedfromthe
USBdrivewithouttheowner’sknowledge.
4.3.3 – TPM+PIN
InthisauthenticationmodetheTPMfirstvalidatestheearlybootcomponents.Ifthischeck
issuccessful,theuserisrequestedtoentertheirPINcode4‐20digitswhichwereentered
‐14‐
when BitLocker is first enabled. Once the PIN is verified, the OS will start. The PIN is
stored within a secure storage area of the TPM and is protected by anti‐hammering
techniques. This protects against brute‐force attacks on the PIN by making the TPM
inaccessibleforaperiodoftimewheneverthewrongPINisentered.Themoretimesthe
PINisenteredincorrectly,thelongertheperiodofinaccessibility24.Thismodeprotects
againstmanyhardwareattacksbutmaystillbevulnerabletospecializedTPMattacks.
4.3.4 – TPM+USB
ThismodevalidatestheearlybootcomponentsandthenrequirestheusertoenteraUSB
drive before they are allowed to boot to Windows. This mode protects against many
hardwareattacksandTPMattacksbutsuffersfromthesamerisksassociatedwiththeUSB‐
onlymode.
4.4 – Boot Integrity Validation (Secure Startup)
The secure startup feature of BitLocker uses the TPM to verify the integrity of the boot
components. The TPM contains a number of Platform ConfigurationRegistersPCRs
which,uponpower‐up,areallinitializedtozero.ThevalueofeachPCRcanonlybe
modifiedbycallingit’s
extendfunctionwhichsetsthevalueofthePCRtobethehashofits
oldvalueandasupplieddatastring25.Whatthiseffectivelymeansisthatthefinalvalue
ofaparticularPCRwillbethehashofallthedatastringssuppliedtoit’s
extendfunction.
Theonlywaythisvaluecouldeverberepeatedistosupplyidenticaldatastringsasbefore
totheextendfunctionintheidenticalorderafterpower‐upofthecomputer.
WhenBitLockerisfirstenabledinoneoftheTPMauthenticationmodes,thecomputerwill
rebootandduringthebootprocessthePCRswillkeeptrackofanybootcodethatruns
includingBIOScodeandtheMBR.TheTPMwillthensealtheBitLockerencryptionkey
basedonthevaluesofthePCRs.ThesealfunctionalsoensuresthatonlytheTPMthat
sealed the key is able to unseal it. Subsequent boots should produce exactly the same
valuesinthePCRsandtheTPMwillunsealtheencryptionkey.Anychangesmadetothe
BIOS or boot code will result in the PCRs producing different values.TheTPMisthen

‐15‐
unabletounsealtheencryptionkeyandWindowscannotboot.Thisiswhatensuresthat
theencrypteddrivecannotbeunlockedsimplybyinstallingitinadifferentsystem.
4.5 – BitLocker Encryption Algorithm
The designers of BitLocker looked at a number of different encryption algorithms 25
beforedecidingtousetheAdvancedEncryptionStandardAES26.AEShasbeensubject
toextensiveanalysisandisconsideredtobeoneofthemostsecurealgorithmsavailable
and also managed to fulfill the performance requirements of BitLocker. AES is used in
cipher‐blockchainingCBCmodewiththeadditionofan“elephant”diffuseralgorithmin
which two diffusers work in opposite directions. The purpose ofthediffuseristhat“it
ensuresthatevenminutechangestotheplaintextresultintheentiresectorchanginginthe
encryptedciphertext”27.Encryptionisperformedonaper‐sectorbasiswherethesector
numberisusedasanextraparameterintheencryption.Thisensuresthatevenifidentical
dataiswrittentodifferentsectorsofthedrive,thosesectors will end up containing
differentciphertexts.Figure4.1showsanoverviewoftheAES‐CBCdiffuserencryption
process:
Figure4.1‐AES‐CBC+DiffuserEncryptionProcess
‐16‐
Thestepsoftheprocessareasfollows:
1. Theunencryptedsectori.e.theplaintextisexclusive‐oredwiththesectorkey
2. Thisisthenrunthroughthediffuserthereareactuallytwodiffusers–oneforeach
direction
3. TheresultisthenencryptedwithAESinCBCmodeproducingtheencryptedsector
ThefullvolumeencryptionkeyFVEKisthe512‐bitkeywhichisusedtoencryptthedrive
sectors.Itisactuallyasplitkeyconsistingoftwo256‐bitkeys–onekeyforderivingthe
sectorkeyandtheotherkeytouseintheAES‐CBCcomponentoftheencryption.Whilstthe
technical details of the encryption process are outside the scope of this project, it is
important to note that as the sector key component and the AES‐CBC component are
independently keyed, BitLocker is
at least
assecureasAES‐CBC.Fulldetailsofthe
encryptionprocessareavailableinapaperbyMicrosoft’sNielsFerguson25.BitLocker
canbeusedinthefollowingmodes:
• AES‐128withdiffuserdefaultmodeforBitLocker
• AES‐256withdiffuser
• AES‐128nodiffuser
• AES‐256nodiffuser
4.6– BitLocker Keys
As mentioned previously, the FVEK is the most important key in the BitLocker key
hierarchyasitisthekeythatisusedintheencryptionanddecryptionprocessfor every
sectoronthedrive.BitLockerstorestheFVEKonthediskaspartofthevolumemetadata.
Three copies of the volume metadata are written to a BitLocker drive in the interest of
redundancy27.TheFVEKcanobviouslyneverbewrittentothediskinanunencrypted
form.Instead,itisfirstencryptedwiththevolumemasterkeyVMKbeforebeingstored.
The VMK is also encrypted and can only be decrypted by one of the “key protectors”
describedinSection4.3.MicrosoftdecidedtousethetwokeysFVEKandVMKsothatthe
BitLockerinstallation could be re‐keyed withouthavingtore‐encryptallthedataonthe
‐17‐
drive. Changing the BitLocker key effectively means changing the VMK that protects the
FVEK.
4.7– Enabling BitLocker
VistaUltimateandEnterprisedonotcomewithBitLockerenabled by default. Access to
enablingBitLockercanbefoundBitLockerDriveEncryptionentryintheControlPanel.A
defaultVistainstallationwillnotallowBitLockertobeenabledunlessthecomputerhasa
TPM.ToallowtheoptiontoenableBitLockerwiththeUSB‐onlyauthenticationmode,the
usermustfirstperformthefollowingsteps:
1. Press the Start button and in the “Start Search” box type ‘
gpedit.msc’ without
quotestoopenthegrouppolicyobjecteditor.
2. Navigate to Local Computer Policy ‐ Computer Configuration ‐ Administrative
Templates‐WindowsComponents‐BitLockerDriveEncryption.
3. Double‐click the “Control Panel Setup:Enableadvancedstartupoptions” entry in
theright‐handpane.
4. Click the “enabled” radio button. Ensure “Allow BitLocker withoutacompatible
TPM”ischeckedandpressApply.
5. Close the group policy editor andopenacommandpromptbypressingtheStart
buttonandinthe“StartSearch”boxtype‘
cmd’withoutquotes.
6. In the command prompt use the command
gpupdate /forcetoupdatethelocal
grouppolicysettings.
Aftertheabovestepshavebeencompleted,theusermayenableBitLockerintheUSB‐only
mode.WhenenablingBitLockerforthefirsttime,theusermusteithersaveacopyofthe
recoverypassword,orprintacopydiscussedlater.Figure4.2 shows the screen
prompting the user to either save or print the recovery password.Oncethishasbeen
completed, the computer then restarts and begins the encryptionprocessinthe
background.

‐18‐
Figure4.2‐BitLockerPrompttoSaveRecoveryPassword
In addition to providing the BitLocker Drive Encryption entry in the Control Panel,
Microsoft has also included a WSF script
manage-bde.wsf which resides in
C:\Windows\System32.ThisistheBitLockerCommand‐lineInterfaceCLIallowsaccessto
enablingBitLockernotonlyontheOSvolume,butalsoonanyothervolumestheuser
wishestoencrypt except the system volume holdingtheunencrypted files used to start
theOS.AswellasprovidingaccesstoenablingBitLocker,thisscripthasmanyotheruseful
featuresandwillprobablyprovetobeanessentialpartofanyliveresponsetoolkit.Alistof
usefulcommandsforthescriptcanbefoundinAppendixD.
4.8–BitLocker Startup Keys
ManyusersofVistaUltimate/EnterprisewillnothavetheTPMhardwarerequiredtorun
BitLockerinanyoftheTPMauthenticationmodes.Inthiscase,theycanonlyrunBitLocker
intheUSB‐onlymode.Thestartupkeyisabinarykeyheldina124‐bytehiddenfileonthe
USB drive which has the filename format
XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX.BEK
whereeachXisahexadecimaldigit.IfBitLockerisenabledintheUSB‐onlymode,thiskey
canbeusedtounlockthedriveonanothercomputer.

‐19‐
4.9–BitLocker Recovery Passwords and Keys
The security features implemented in BitLocker mean that it is currentlynotpossibleto
decrypt an encrypted drive without the presence of the correct key protector. However,
duringtheprocessofenablingBitLocker,theuserisrequiredtoeithersaveand/orprinta
recoverypassword.Therecoverypasswordisa48‐digitnumberthat canbe used inthe
event that something goes wrong duringtheBitLockerstartupprocess. Microsoft has
identifiedanumberofrecoveryscenarios28including:
• LostUSBkey
• ForgottenPIN
• Changetopre‐OSfilese.g.BIOSupgrade
• Broken hardware e.g. TPM breaks and hard drive has to be movedtoanew
system
• Deliberateattackse.g.hackedBIOS,modifiedMBR
Intheeventofarecoveryscenario,theuserispresentedwiththefollowingscreenwhere
theycanentertheir48‐digitrecoverpasswordinordertounlockthedrive:
Figure4.3‐RecoveryPasswordEntry

‐20‐
Inadditiontothismethod,theusercanalsotransferthedrivetoanotherVistaUltimateor
VistaEnterprisesystemandunlockthedriveviaeithertheBitLockercontrolpanelorusing
the
manage-bde.wsf script discussedlater.
48‐digitrecoverypasswordssavedtodiskaresavedinatextfilewiththefilenameformat
XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX.txt where each X is a hexadecimal digit. This
32‐digithexadecimalstringcorrespondstotheadministrativepasswordIDthatisassigned
byBitLockerwhenthedriveisenabled.Thetextfilecontainstherecoverypassword.The
contentsofatypicalrecoverypasswordfileareshowninFigure4.4.
Figure4.4‐ContentsofaTypicalRecoveryPasswordFile
The relationship between the administrative password ID, recovery password filename,
and48‐digitrecoverypasswordareshowninFigure4.5:
Figure1.5‐RelationshipbetweenBitLockerPasswordIDandRecoveryPassword

‐21‐
As well as being able to identify a recovery password file for BitLocker, an investigator
mustalsobe awarethattheusermayhavea printedcopyoftherecoverypassword.An
examplerecoverypasswordprintoutcreatedusingtheBitLockercontrolpanelisshownin
Figure4.6:
Figure4.6‐ExamplePrintedRecoveryPassword
BitLockerrecoverykeyscanalsobecreatedseeSection4.11.BitLockerrecoverykeysare
“cryptographicallyequivalent”29tostartupkeysandcanbeusedtounlockthedrive.
Itisclearthatrecoverypasswords/keysareimportantforwhen something goes wrong
withaBitLockerinstallation.Fromaforensicpointofview,theyareevenmoreimportant.
AphysicalimageofadrivewithBitLockercanbecreatedwithoutanyproblems.However,
aphysicalimageofthedrivewillsimplyholdtheencrypteddata.Thisisofverylittleuse
from an investigative standpoint.Inorderfortheinvestigatortoviewtheunencrypted
data,alogicalimageofthevolumemustbetakenandthisrequirestheuseoftherecovery
password/keytounlockthedrive.Iftheinvestigatorcannotgainaccesstothesystemina
liveresponsescenario,theymustbeawarethatifBitLockerisenabledandthecomputeris
then switched off, it may prove impossible to recover the unencrypteddata.Forthis
reason, it is vitally important in live response scenarios thatremovablemediaand
printoutsareseizedandlatersearchedforBitLockerkeysorpasswords.
4.10–Identifying the Presence of BitLocker
Inaliveresponsescenario,aninvestigatormayapproachamachinethatisrunningVista
andmayhaveBitLockerenabled.Iftheuseraccountsonthemachinehaveapassword,

‐22‐
thefollowingscenariosmayrequireapasswordisenteredbeforetheinvestigatorcangain
accesstothedesktop:
1. ThemachineiscurrentlyloggedoffAlluseraccountsarepasswordprotected.
2. ThemachineiscurrentlylockedAlluseraccountsarepasswordprotected.
3. The machine is in sleep mode By default, Vista has the “Require a password on
wakeup”optionsettoYes.
4. ThemachineisinhibernatemodeBydefault,Vistahasthe“Requireapasswordon
wakeup”optionsettoYes.
5. ThescreensaverforthedesktophasbeenactivatedBydefault,Vistadoesnot
use
the“Onresume,displaylogonscreen”underthescreensaversettings.
Inthesescenarios,withoutobtainingapasswordfromthesuspectorsystemadministrator
itiscurrentlynotpossibletogainaccesstothedesktop.Ifthesystemiscurrentlylogged
on,caremustbetakenthatanyofthesescenariosdonotoccur.Itisalsoimportanttonote
that if investigators approach an unlocked system that is only running a standard user
account, UACwillmakeit impossible to identifythe presenceofBitLockerand/orcreate
recovery keys using any of the methods discussed in this chapter.Inthisscenario,the
investigatorwouldneedtoobtainthepasswordforoneoftheadministratoraccountson
themachinetoelevatetoadministratorstatus.
4.10.1–Identification via BitLocker Command-Line Interface (CLI)
ThebesttechniquetodetermineifBitLockerisenabledistousethemanage-bde.wsfscript
mentionedinSection4.9.Usingthe
–statusparameterprovidestheencryptionstatusof
allvolumes.Thestepsareasfollows:
1. NavigatetoStart‐AllPrograms‐Accessories.Right‐clickonthe“command
prompt”iconandselect“Runasadministrator”whenprompted.Press“continue”in
theUACpopupwindow.
2. Inthecommandprompt,navigateto
c:\windows\system32
3. Runthecommand
cscript manage-bde.wsf –status

‐23‐
Thiswillprovideanoutputsimilartothefollowing:
Figure4.7‐UsingBitLockerCLItoDetermineEncryptionStatus
Thiswilllisttheencryptionstatusofanyvolumesonthesystem.Note:thisscriptwillonly
workwhenrunwithadministratorcredentialsandusingthe“Runasadministrator”action.
Whenrunwithstandardprivileges,theBitLockerCLIproducesthefollowingerror:
Figure4.8‐RunningBitLockerCLIwithStandardPrivileges
4.10.2–Identification via BitLocker Control Panel
The encryption status of any drives can also be determined by checking the BitLocker
controlpanelasfollows:
1. NavigatetoStart‐ControlPanel‐BitLockerDriveEncryption.
2. Double‐clicktheentrytoopentheBitLockercontrolpanel.

‐24‐
Figure4.9showstheBitLockercontrolpanelwithtwoencrypteddrives–theencryptedOS
volume
C:andanencrypteddatavolumeG::
Figure4.9‐BitLockerDrivesShownintheControlPanel
Note:TheBitLockercontrolpanelisonlyaccessiblewithadministratorprivileges.
4.10.3–Identification via Disk Management Snap-In
Thediskmanagementsnap‐incanalsobeusedtoidentifyaBitLockervolume.Thiscanbe
accessedusingthefollowingsteps:
1. PresstheStartbuttonthenrightclickon“Computer”andselect“Manage”.
2. In the Computer Management window select Computer Management Local‐
Storage‐DiskManagementintheleftpane.
3. Thediskconfigurationwillthenloadinthecentrepane.
Figure 4.10 shows a typical BitLocker disk configuration with the small, unencrypted
systempartitionandthelargerencryptedOSvolume:
Figure4.10‐DiskManagementSnap‐InwithBitLockerDrive

‐25‐
4.10.3–Identification Using a Hex Editor
Ablogentry30postedbyJamieHunterofMicrosoft’sSystemIntegrityTeamdescribes
howtoidentifythepresenceofBitLockerbylookingdirectlyatthecontentsofthephysical
disk.Inparticular,themethodinvolveslookingattheBiosParameterBlockBPBwhichis
locatedatthefirst0x54bytesofthefirstsectorofthevolume.Jamieprovidesthefollowing
tabletocheckfortheexistenceofBitLocker:
Table4.1‐BPBCharacteristicsofaBitLockerVolume
Byexaminingthefirstsectorofthevolumeandcheckingallfieldswitha“requiredvalue”,
it is possible to identify BitLocker. This can be achieved using WinHex by using the
followingprocedure:
1. StartWinHex.SelectTools‐OpenDisk
2. Under“PhysicalMedia”selectthedisksuspectedofcontainingaBitLockervolumeand
pressOK
3. ThediskwillnowhaveitsowntabintheWinHexmainwindow.Double click the
partitionsuspectedofcontainingtheBitLockervolume.
4. InspectthediskusingTable4.1asaguide.
Figure4.11showseachofthevaluesfromTable4.1highlightedinWinHex.Redandblue
have been used for highlighting in an alternating fashion for ease of reading. The byte
string “2D 46 56 45 2D 46 53 2D” corresponds to the “Signature”fieldoftheBPB.The
string“0202”correspondstothe“BytesPerSector”fieldandsoon.

‐26‐
Figure4.11‐BPBValuesHighlightedinWinHex
Note:Administrativeprivilegesarerequiredtolookatthephysicalviewofthedisk.
4.11–Viewing and Creating BitLocker Recovery Passwords/Keys
Section4.9describedtheimportanceoftherecoverypasswords/keysforadrive.Duringa
liveresponse,iftheinvestigatorhasaccesstotheVistadesktopwithanaccountthathas
administratorprivileges,itispossibletoviewtherecoverypasswordforadriveorcreatea
backupoftherecoverykeys.
4.11.1–Viewing Key Protectors via BitLocker CLI
Toviewthecurrentkeyprotectorsforadrive,usethefollowingprocedure:
1. NavigatetoStart‐AllPrograms‐Accessories.Right‐clickonthe“command
prompt”iconandselect“Runasadministrator”whenprompted.Press“continue”in
theUACpopupwindow.
2. Inthecommandprompt,navigateto
c:\windows\system32
3. Togettheprotectorsforthe
C:drive,werunthecommand
cscript manage-bde.wsf–protectors –get C:
4. Protectorsforotherdrivescanbeobtainedbysimplychangingthedriveletter.
Thiswillprovideanoutputsimilartothefollowing:

‐27‐
Figure4.12‐ViewingKeyProtectorsforaDrive
Thenumericalpasswordshouldbenotedasitcanbeusedlatertounlockadriveforlogical
imaging.
4.11.2–Obtaining Recovery Keys via BitLocker CLI
Copiesofanyrecoverykeyscanbecreatedusingthefollowingprocedure:
1. NavigatetoStart‐AllPrograms‐Accessories.Right‐clickonthe“command
prompt”iconandselect“Runasadministrator”whenprompted.Press“continue”in
theUACpopupwindow.
2. Inthecommandprompt,navigateto
c:\windows\system32
3. TocopytheprotectorsfortheC:drive,werunthecommandcscript manage-
bde.wsf –protectors –get C: -sek G:\KeyBackup
ThiswillcopytherecoverykeysfordriveC: tothelocationG:\KeyBackup.Thedriveletter
andsavepathcanbeamendedasnecessary.Atypicaloutputfromrunningthecommandis
showninFigure4.13.Investigatorsshouldnotethatthiscommanddoesnotmakeacopyof
thenumericalpassword.Thismustbenotedmanually.

‐28‐
Figure4.13‐SavingRecoveryKeystoExternalLocation
4.11.3–Obtaining Recovery Keys via BitLocker Control Panel
CopiesoftherecoverykeyscanalsobeobtainedbyusingtheBitLocker control panel
Control Panel‐BitLocker Drive Encryption. By clicking “Manage BitLocker Keys”
beneaththeencryptedOSentry,itispossibleto:
• DuplicatetherecoverykeytoaUSBdrive
• Duplicatetherecoverykeytoafolder
• Printtherecoverypassword
• ResetthePINforTPMPINmode
4.11.4–Other Sources of Recovery Keys
WindowsActiveDirectorycanbeconfiguredtoremotelystorerecoverykeys.Thisfeature
isusedtoallowadminstocontrolaccesstorecoverykeysandsilentlybackupanycreated
recovery keys to Active Directory. Investigators should be aware that in enterprise
environments with Active Directory, the IT administrator may have access to recovery
keys.Fulldetailsareavailablefrom31.
Windows Ultimate Extras are a series of free add‐ons available for Vista Ultimate via
Windows Update. One of these is the “BitLocker and EFS Enhancements” extra. This

‐29‐
providesanew“SecureOnlineKeyBackup”featureseeFigure4.14allowingtheuserto
store a copy of their recovery password and Encrypting File System EFS recovery
certificatesusingWindowsonlineDigitalLocker32.Therecoverykeysareobtainedby
loggingintoWindowsMarketplaceusingtheuser’sWindowsLiveID.
Figure4.14‐SecureOnlineKeyBackup
4.12–Working with BitLocker Images
A BitLocker drive should be imaged by connecting the drive to a forensically‐secure
workstation running either Vista Ultimate or Enterprise and usingawrite‐blocker.An
physicalimageofthediskcanbetakenifnecessary.However,itshouldbenotedthatthisis
animageoftheencrypteddata.Toprovideanimagethatanexaminercanactuallywork
with,alogicalimageofthevolumemustbetaken.Beforecreatingalogicalimage,thedrive
mustfirstbeunlockedwhichrequirestherecoverykeysforthedrive.Unlockingthedrive
canbeachievedbyusingeithertheBitLockerCLIorusingtheBitLocker control panel.
Onceunlocked,thelogicalimagecanbecreatedusingtoolssuchasFTKImager6.It
shouldbenotedthatsuchtoolsmustberunwithadministratorprivileges.
4.12.1–Unlocking via the BitLocker Control Panel
The BitLocker control panel allows unlocking of an encrypted drive using either the
recoverypasswordortherecoverykey.ThisisaccessedusingStart‐Control Panel‐
BitLockerDriveEncryption.TheexaminerthenhastheoptiontounlockanyBitLocker
encryptedvolumes:

‐30‐
Figure4.15‐UnlockingusingBitLockerControlPanel
Windowsthengivestheoptionto“Loadpasswordfromremovablemedia” or “Manually
inputthepassword”.Loadingthepasswordfromremovablemediarequirestherecovery
keyfile
*.BEKtobecontainedintherootofaremovableUSBdevice.Itshouldbenoted
thatthe
.TXTfilecontainingthe48‐digitrecoverypasswordwillnotunlockthedriveusing
thisoption.However,thepasswordcontainedinthefilewillunlockthedrivebyselecting
the“Manuallyinputthepassword”optionandtypingthe48‐digitcodeintothetextbox.
4.12.2–Unlocking via the BitLocker CLI
TheBitLockercommand‐lineinterfacecanbeusedtounlockanencrypteddrivebyusing
eithertherecoverypasswordortherecoverykey.Unlockingusingtherecoverypassword
isasfollows:
1. NavigatetoStart‐AllPrograms‐Accessories.Right‐clickonthe“command
prompt”iconandselect“Runasadministrator”whenprompted.Press“continue”in
theUACpopupwindow.
2. Inthecommandprompt,navigateto
c:\windows\system32

‐31‐
3. TounlocktheE:drive,werunthecommandcscript manage-bde.wsf –unlock E:
-RecoveryPassword XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-XXXXXX-
XXXXXX
4. Thedrivelettercanbeamendedtosuittheexaminersneeds.Thelastargumentto
thecommandshouldobviouslybereplacedwiththe48‐digitrecoverypassword
specifictothedrivebeingunlocked.
Figure4.16showsatypicaloutputfromrunningthecommand:
Figure4.16‐UnlockingusingBitLockerCLI&Password
Thefollowingmethodisusedtounlockusingarecoverykey:
1. NavigatetoStart‐AllPrograms‐Accessories.Right‐clickonthe“command
prompt”iconandselect“Runasadministrator”whenprompted.Press“continue”in
theUACpopupwindow.
2. Inthecommandprompt,navigateto
c:\windows\system32
3. TounlocktheE:drive,werunthecommandcscript manage-bde.wsf –unlock E:
-RecoveryKey <file>
4. Thedrivelettercanbeamendedtosuittheexaminersneeds.Thelastargumentto
thecommandshouldbethefilenameincludingfullpathoftherecoverykey.This
partshouldbeenclosedininvertedcommasifthereareanyspacesinthe
path/filename.
Figure4.17showsatypicaloutputfromrunningthecommand

‐32‐
Figure4.17‐UnlockingusingBitLockerCLI&RecoveryKey
4.13–Attacking BitLocker
DouglasMacIveroftheMicrosoftPenetrationTeamgaveapresentation33atthe2006
HackintheBoxsecurityconference.Thisoutlinedanumberofpossibleattackvectorsfor
gainingaccesstoanencryptedBitLockervolume.Duringextensive testing, the team did
notmanagesuccessfullyunlockthedrivethroughanattack.NitinandVipinKumar,owners
oftheIndiansecurityfirmNVLabs34,wererecentlyscheduledtogiveapresentationat
the Black Hat security conference regarding their TPMkit softwareabstractavailableat
35.TheyclaimtohavedevelopedamethodtocircumventtheTPM checksduringthe
secure startup of a BitLocker system. The presentation was later controversially
withdrawn at the request of the Kumar brothers 36. As it stands, there have been no
knownsuccessfulattacksonaBitLockersystem.

‐33‐
Chapter 5
Thumbnails
ThischapterbeginsbyoutliningthecachingsystemthatwasusedinWindowsXP.Itthen
describeshowthishaschangedinVistaandhowanexaminercanextractthumbnailsfrom
thenewcache.Thechapterconcludesbydetailingpartofthefileformatusedforstoring
thumbnailsintheVistathumbcachefilesandhowthiscanbeusedtofindextrainformation
abouttheoriginalfile.
5.1 – Thumbnails in Windows XP
ThumbnailviewsinWindowsshowaminiatureviewofalargerimage,allowingusersto
quicklyscanthroughalargenumberofimages.Someofthefile formats XP stores as
thumbnailsincludethefollowing37:
JPEG,BMP,GIF, TIF,PDFandHTM. Thumbnailviews
could be accessed in an XP Explorer window by using View‐Thumbnails. This would
displayanygraphicsinthatfolderasthumbnailsratherthanthe icon views normally
associatedwiththefiles.Whenafolderhadthethumbnailviewenabledandcontaineda
“thumbnailable”format,ahidden file
thumbs.dbwasautomaticallycreated.Thisfileisa
databaseofthethumbnailsforthatfolderwitheachthumbnailbeingstoredinthedatabase
as a
JPEGfile,regardlessofthefile’soriginal format 38. In addition to storing the
thumbnailimageoftheparentfile,XPalsostoresthefilename.Whenanentryisaddedto
thethumbs.db,itstaysthereindefinitelyeveniftheoriginalfileisdeleted.Thismeansthat
anXPuserhastoeitherdeletethe
thumbs.dbfileitselforthefolderthatholdsitinorder
toremovetracesofanygraphicsthathavebeenstoredinthefile.ToolssuchasFTK39
are able to display the thumbnails contained in the
thumbs.dbfileaswellastheparent
filenameandmodifieddateof theparentfile.Fulldetailsof
thumbs.dbfilesandworking
withtheminFTKareavailableat38.

‐34‐
5.2 – Thumbnails in Windows Vista
Thumbnailssometimesreferredtoas“LiveIcons”inVistanowallowscalablethumbnails
ofafileandshowapreviewoftheactualcontentsofafileorfolder,ratherthanthegeneric
programiconsusedinXP.Figure5.1showstwoviewsofafoldercontaininganotherfolder
andfourfiles:twojpegimagesandtwoPDFfiles.Theleftwindowshowsthe“List”viewin
Vista and uses the traditional program icons. The right window shows the “Large Icons”
viewandshowsapreviewofeachofthefilesaswellasapreviewofthecontentsofthe
folder.UserschangethesizeoftheiconsusedbyclickingtheViewsbuttononthefolder
toolbarandmovingasliderupanddowntoincrease/decreasethesizeoftheiconsused.
Selectinganysizefrom“MediumIcons”andabovewillpreviewthecontentsofthefile,as
willusingthe“Tiles”view.
Figure5.1‐DifferentViewsinWindowsVista
Vistahasremovedtheneedtocreateathumbs.dbfileonaper‐folderbasis.Instead,ituses
acentralizedthumbnailcacheforeachuserlocatedat:
C:\Users\<username>\AppData\Local\Microsoft\Windows\Explorer
TherearefourthumbnailcachesasVistastoresthumbnailimagesinasetofdiscretesizes
40.Thesizesinpixelsare32x32,96x96,256x256,and1024x1024.Thecorresponding
cachefilesarenamed:
• thumbcache_32.db
• thumbcache_96.db

‐35‐
• thumbcache_256.db
• thumbcache_1024.db
Duringtesting,thefileswerefoundtocontainembeddedJPG, BMP,andPNG files.These
wereextractedusingthe“DataCarve”featureofFTKv1.71.Table5.1explainsthecontent
ofthefilesfoundduringtesting.Figure5.2showsFTKafterperforming a data carve on
thumbcache_1024.db.
File Contents
thumbcache_32.db
Storesthumbnailsupto32x32pixels.Duringtesting,all
thumbnailswerestoredinBMPformat.TheBMPfilesheld
previewsofbothfilesandfolders.
thumbcache_96.db
Storesanythumbnailslargerthan32x32pixelswithmaximum
dimensionsof96x96pixels. Duringtesting,allthumbnailswere
storedinBMPformat.TheBMPfilesheldpreviewsofbothfiles
andfolders.
thumbcache_256.db
Storesanythumbnailslargerthan96x96pixelswithmaximum
dimensionsof256x256pixels.Duringtesting,thumbnailswere
storedinamixtureofJPGandPNGformats.TheJPGfilesstored
previewsoffilesandthePNGfilesheldpreviewsoffolders.
thumbcache_1024.db
Storesanythumbnailslargerthan256x256pixelswithmaximum
dimensionsof1024x1024pixels.Duringtesting,allthumbnails
werestoredinJPGformat.TheJPGfilesstoredpreviewsoffiles.No
previewsoffolderswerestored.
Table5.2‐Contentsofthumbs.dbFilesDuringTesting
Figure5.2‐FTKPreviewfromthumbcache_1024.db

‐36‐
The test data used during experimentation was obtained from three different Vista
installations–twoUltimateinstallationswhichhadbeenusedforthemajorityoftestingin
thisdocumentandaHomePremiuminstallationwhichhadbeenusedforgeneraleveryday
useforapproximatelythreemonths.Severalspecifictestcaseswerealsosetup.Thesetest
caseswereusedtocheckforcachingofthumbnailsforfileson removable devices and
networkeddevices.ItwasfoundthatVistacachesthumbnailsinboththesecases.
5.3 – Thumbcache File Format
Duringtesting,thevastmajorityofthumbnailsheldinthethumbcachefileshadafilename
oftheformat
XXXXXXXXXXXXXXXX.<ext>whereeachX is a hexadecimaldigitand <ext>is
either
BMP,JPGorPNG.Therewereafewcaseswherethefilenamehadstayedthesameas
theparentfilewiththe
.<ext>partthenappended.
Inspectionofthethumbcachefileswithahexeditorrevealedsomeinterestingfeaturesof
the caching. The embedded JPG, BMP, and PNG files could be foundbysearchingforthe
appropriatefileheadersforeachformate.g.
0xFFD8FFE000104A464946foraJPG.Before
theheaderforthefilethereisablockofmetadata.Thestartofthemetadataisidentifiedby
the4‐bytehexstring
0x434D4D4D.Followingthisthereareanother4bytes,thepurposeof
whichareunknown.The8bytesafterthatcontainauniqueidentifierforthefile.Thelast
32bytescorrespondtothehexadecimalnamegiventothethumbnail file except in the
rarecasethethumbnailhasretainedthefilenameoftheparentfile.Every2
nd
byteofthis
32‐bytefilenamesectionispaddedwith
0x00effectivelyleaving16bytesforthefilename.
The size of this metadata block varies, even between cases where thumbnails are being
storedinthesameimageformat.Figure5.3showswhichpartsofthethumbnailmetadata
remainconstant.Anysectionswhichhavevaryinglengthsaredenotedby“
?bytes”.
Figure5.3‐ThumbnailMetadataFormat
‐37‐
Inside the C:\Users\<username>\AppData\Local\Microsoft\Windows\Explorerfolder
there is also an index file named
thumbcache_idx.db.Ifwesearchtheindexfileforthe
uniqueIDofoneofthethumbnailscontainedintheotherfourfiles,weshouldfindamatch.
The8bytesthatfollowthematchinguniqueIDgiveusthe8‐byteWindowsFILETIMEvalue
forwhentheparentfilewascreatedi.e.thefilethethumbnailwascreatedfrom.During
testing,athumbnailviewfortheimagein Figure 5.4 was created.Figure5.5onpage38
showsthethumbnailinFTKthenthecorrespondingentriesin
thumbcache_256.dband
thumbcache_idx.db.
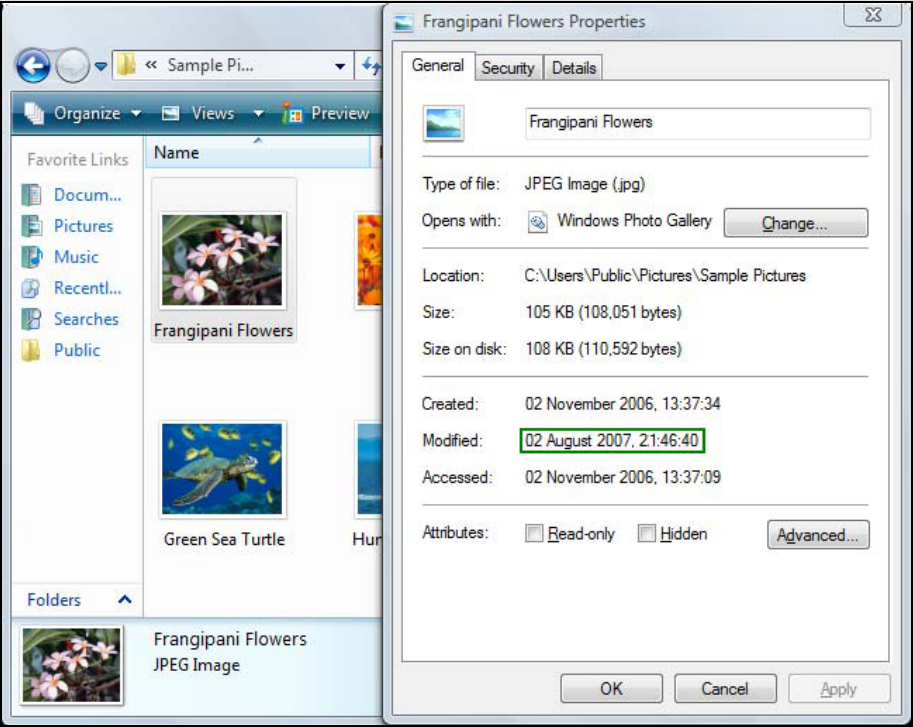
Figure5.4–FilePropertiesofParentImage

‐38‐
Figure5.5‐ThumbnailEntryinHexEditor

‐39‐
Chapter 6
User File Activity in Vista
Thischapterdescribesthechallengesfacinginvestigatorswhenexaminingfileactivityina
WindowsVistasystem.Itthengoesontodescribeanumberofmethodswhichcanbeused
inhelpingtogainaninsightintoauser’sfileactivity.
6.1 – Windows XP and Last Access Times
FilesonanNTFSvolumecontainaLastAccessTimeattributeshowingwhenthatfilewas
lastaccessed.ThisattributeisupdatedbydefaultonWindowsXP.Whenafileisaccessed,
theNTFSfilesystemupdatesthelastaccessedattributeinmemoryandlaterwithadelay
ofuptoonehourwritestheattributetodisk4142.Evenwiththispotentialdelayofup
toonehour,theLastAccessTimeattributehasbeenavaluable source of evidence by
allowing investigators to build approximate timelines of file activity. This is useful in
helpingtobuildaprofileofanoffender’sactivityandgiveanideaoftheordereventsmay
haveoccurred.
6.2 – Vista and Last Access Times
During the development of Vista,Microsoftdecidedtodisablethe updating of the Last
Access Time file attribute by defaulttoimproveNTFSperformance 43. While this may
improve performance for the end‐user, it provides a headache for forensic examiners as
creatingtimelinesoffileactivityisnolongerpossible.Examinersmustnowemployother
methodstobuildaprofileofuseractivity.
6.3 – Recent Items Folder
Windows XP kept a record of files and folders recentlyopened by theuser. These were
stored as shortcuts in the
C:\Documents and Settings\<username>\Recentfolder.Vista
continuesthisbehaviourbystoringshortcutstorecentlyaccessedfilesandfoldersinthe
C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Recent Items folder.

‐40‐
Whenarecentlyaccessed file/folderis addedtotherecentitemslistforthe first time,a
shortcutiscreated.Wheneverthatfile/folderissubsequentlyopened,thecreateddatefor
thecorrespondingshortcutstaysthesamebutthemodifieddateoftheshortcutisupdated.
Byexaminingtheshortcutsandtheirmodifieddates,aninvestigatorcandeterminesome
ofthefilesthathavebeenrecentlyaccessedandatwhattimetheywerelastaccessed.
6.4 – Recently Executed Programs
Vistamaintainsarecordofrecentlyexecutedprogramsinthefollowingregistrykey:
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{75048700-EF1F-
11D0-9888-006097DEACF9}\Count
Whenaprogramisexecutedforthefirsttime, avalueiscreatedintheregistrykey.The
valuenameisstoredinROT13formateachletterrotatedby13places.Thenameconsists
ofastringidentifyingthetypeofcommandfollowedbythenameoftheexecutable.During
testing,thefollowingcommandidentifierswerefound:
CommandIdentifier Description
UEME_CTLCUACount
Unknown.
UEME_CTLSESSION
Unknown.
UEME_RUNPATH
Executablesrunonthecomputer.
UEME_RUNPIDL
Executablesaccessedviathestartmenuandwebpagesaccessed
usingtheStart‐StartSearchentrydialog.
Table6.3‐CommandIdentifiersandDescriptions
Anexamplevaluenameforthe
UEME_RUNPATHcommandidentifierisshownbelow:
UEME_RUNPATH:C:\Program Files\AccessData\AccessData FTK Imager\FTK Imager.exe
Thevaluedatathencontainsacounterofhowmanytimestheprogramhasbeenexecuted
and the date and time of when it was last executed. Any executables that have been
launchedbyusingStart‐StartSearchandenteringthe executablenametaketheformat
of:
UEME_RUNPATH:%csidl0%<executable>" "
‐41‐
UEME_RUNPIDL entriesappeartobeprogramswhichhavebeenlaunchedvialinks in the
startmenu.TheseentriesarealsousedtomaintainarecordofURLstypedintotheStart‐
StartSearchdialogthisthenlaunchesthecomputer’sdefaultwebclientandnavigatesto
thepage.Reference44outlinessomeworkperformedonexaminingtheuserassistkeys
onaWindowsXPsystem.Viewingtheuserassistkeysismadeeasierbyusingatoolwhich
automaticallyretrievesanddecryptstheentriessuchasUserAssistv2.3.045.
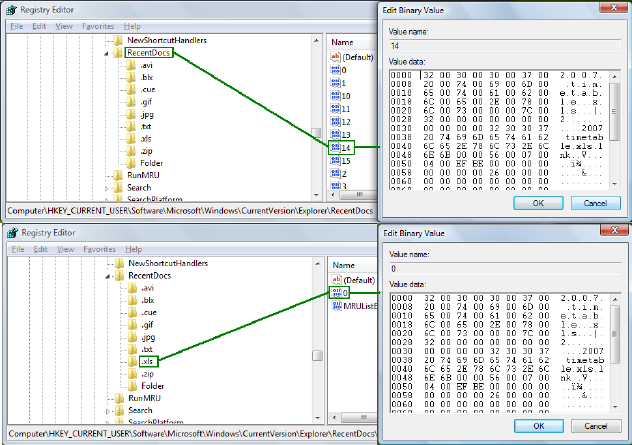
6.5 – Vista RecentDocs Key
Inadditiontomaintainingalistofpreviouslyexecutedprogramsintheuserassistkeys,
Vistaalsostoresalistofrecentlyuseddocumentsintheregistryinthefollowingkey:
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
Recently accessed documents are added to this key as binary values and are numbered
sequentiallyinorderofwhentheywerefirstaccessed.Ifafileisaccessedagain,itretains
itsoriginalvaluename.TheRecentDocskeyalsocontainsanumberofsubkeys.Theyare
named after the filename extensions of any files added to the recent documents list. In
effect, each entry in RecentDocs will have another entry in its corresponding extension
subkey.ThisisshowninFigure6.1:
Figure6.6‐RegistryEntryinRecentDocsandCorrespondingEntryinSubkey

‐42‐
6.6 – The Windows Search Indexer
VistahasusestheSearchIndexertospeeduptheresultsofusersearches.Bydefault,Vista
indexesthecontentsofthe
UsersfolderandtheStart Menufolder.Theactivityofthe
search indexer process
SearchIndexer.exe was monitored using Process Monitor 4.
Theprocessperformedwritestofileslocatedinthefollowingfolderanditssubfolders:
C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Projects\SystemIndex\
Of the files examined, only one appeared to contain any useful information. The file is
containedinthe folderaboveandhas afilename in the format
SystemIndex.NtfyX.gthr
where the
X is replaced by a decimal number. When viewed with a hex editor,thefile
containsa67‐bytefileheaderwhichshowsthefileisa“Microsoft Search Gatherer
TransactionLog.FormatVersion4.9”.Afterthisheader,thelogfileisthensplitupinto
entries.Eachentryappearstocontaindetailsoffilesandfoldersthathavepassedthrough
theindexer.Duringtestingwiththelogfile,allentrieswereregardingfilesorfoldersfrom
indexed locations. Experimentation showed that a new entry was often appended tothe
endofthelogfilewheneverfoldersorfileswereopened.Thisheldtrueforthemajorityof
filesandfoldersusedinindexedlocations.Nodocumentationforthelogformatcouldbe
found online. Examination of sample log files revealed that each entry is split into three
blocks.Theseblockstakethefollowingformat:
Figure6.2‐FormatofEntriesinGathererLogFile
‐43‐
Eachentrystartswitha48‐byteheaderblock.Theheaderblock contains the following
information:
•
<HEADER_ID> –Headerblockidentifier0x4D444D444bytes
•
UNKNOWN ‐12bytes
•
<TIME_1> ‐WindowsFILETIMEEntry8bytes
•
<TIME_2> ‐WindowsFILETIMEEntry8bytes
•
<CONST_1> ‐Constant0x02000000000000008bytes
•
UNKNOWN ‐8bytes
Aftertheheader,thereisablockholdingthepathandnameofthefile/folderthelogentry
wascreatedfornotethisblockisnotfixed‐length:
• <FILENAME> ‐Thenameandfullpathofthefile/foldervaryingsize
After the filename block, there is an 89‐byte footer block containing the following
information:
•
<FOOTER_ID> ‐Footerblockidentifier0x000000000000000000FFFFFFFF4bytes
•
<TIME_3> ‐WindowsFILETIMEEntry8bytes
•
<CONST_2> ‐Constant0xFFFFFFFF4bytes
•
<TIME_4> ‐WindowsFILETIMEEntry8bytes
•
UNKNOWN ‐20bytes
•
<TIME_5> ‐WindowsFILETIMEEntry8bytes
•
<TIME_6> ‐WindowsFILETIMEEntry8bytes
•
UNKNOWN ‐20bytes
Totesthowentriesgointothefile,amixtureoffileandfolderoperationswereperformed
created/opened/modified/closed.Theorderinwhichthefiles/folderswereusedaswell
‐44‐
astheapproximatetimewasrecorded.Themajorityoffilesusedintestinghadnewentries
addedtothelogfileoftenmultipleentriesandthetimefieldsintheheaderandfooter
blocksfortheentriesreflectedtheapproximatetimeeachfilewasusedin testing.Inthe
test cases, the fields
<TIME_1>and<TIME_2> always contained valid Windows FILETIME
entries. The remaining time fields were populated with valid filetimes in the majority of
testcases,althoughinsomeinstancesthefieldscontainedeither
0x0000000000000000or
0x0100000000000000.
Inspection of this file may give examiners an idea of an offender’s file activity and
approximate times for when files were accessed. Due to time constraints, no additional
testingcouldbeperformedonthelogfile.
6.7 – SuperFetch
TheWindowsXPPrefetcherwasusedtospeedupbootandapplicationlaunchtimes.Vista
hasintroducedSuperFetchwhichtakesthisideafurtherbyanalysingusagepatternsovera
periodoftime.AsauserusesVista,SuperFetchbuildsahistoryoftheirusagepatternand
keepstrackofinformationsuchastheforegroundapplicationbeingused,timeofday,and
dayoftheweek46.ThisallowsVistatoderivetheoptimalmemorycontentforauser
basedontheirusagehistoryandattemptstopro‐activelypopulatethememorywiththis
content. While XP was only used for speeding up boot and application launch times,
SuperFetchtakesamorebroadapproachandwillalsomonitorwhatdocumentsauser
frequentlyaccesses47.
SuperFetch stores its files in the
C:\Windows\Prefetch folder. The folder contains a
number of prefetch files with a
.pf extension. The filenames of the prefetch files are
composedof48:
• Thenameoftheapplication
• Adash
• Aneightcharacterhasofthelocationfromwhichtheapplicationwasrun
• The
.pf extension
‐45‐
Wheneveranewapplicationisexecutedforthefirsttime,acorresponding.pffilewillbe
created in the prefetch folder. Any time thereafter that same program is executed, the
modified date for the
.pf file is updated. If the application is then uninstalled, the
corresponding prefetch entry still remains in the prefetch folder.Thisisusefultoan
investigatorasitletstheminfer:
1. Whatapplicationshavebeenexecutedonthecomputerbycheckingthefilenames
oftheprefetchfiles
2. When the application was first executed the created date of the corresponding
prefetchfile
3. When the application was last executed the modified date of the corresponding
prefetchfile
Inadditiontoholdingthe
.pfprefetchfiles,theprefetchfolderalsocontainsanumberof
usage scenario files 49 of the form
Ag<X>.dbwhere<X>canbeanumberofstrings
dependingonthesystem.Vistainstallationsseemcreatethefollowingscenario files by
default:
AgAppLaunch.db, AgGlFaultHistory.db, AgGlFgAppHistory.db, AgGlGlobalHistory.db,
and
AgRobust.db.Eachuseraccountonthesystemthenappearstohaveitsownscenario
filescreatedwhichtaketheform
AgGlUAD_P_<SID>.dbandAgGlUAD_<SID>.dbwhere<SID>
istheuser’sSecurityIdentifier.Theformatofthesefilesisunknownandthereiscurrently
noMicrosoftdocumentationthatgivesanycluestodescribingthem.Ifthesefilescontain
the usage patterns for a user, they could prove to be useful ininvestigations.Further
investigationwouldhoweverbeneeded.

‐46‐
Chapter 7
Backup Features in Vista
ThischapterdescribeshowVistausesshadowcopiestoallowusers to restore previous
versionsoffilesandthepositiveimpactthismayhaveoninvestigations. It then gives a
briefoutlineofsomeoftheotherbackupfeaturesinVista.
7.1 – Restore Previous Versions
RestorePreviousVersionsisavailableintheBusiness,Enterprise,andUltimateeditionsof
WindowsVista50.Whenaninadvertent changeor deletion of a fileorfolderoccurs,a
usercanuseRestorePreviousVersionstorevertthefileorfolderto a previous state. It
worksbyusingtheVolumeShadowCopyServiceVSStotakesnapshotsofchangesmade
tofilesupto64versionsofthefilecanbestoredinthesnapshotdatabase51.VSSuses
a copy‐on‐write differential copy method to maintain the backups used for previous
versions12.Insteadofhavingtostoreacompletecopyofafileeverytimeitischanged,
VSStracksonlythechangesmade.ThisallowsVSStocreateshadowcopiesoffilesquickly
asitonlyhastowritethechangestodisk52.
ShadowcopiesareenabledbydefaultinVistaandareautomaticallycreatedforthesystem
volumeallfilesaremonitored,althoughothervolumescanbeenabledusingtheBackup
andRestoreCentre in theControl Panel.The user can access previousversionsbyright‐
clickingonafileorfolderandselectingthe“Restorepreviousversions”option.Thisthen
bringsupadialogboxshowinganypreviousversionsofthefile.Figure7.1onpage47
showsthepreviousversionsforafolder“ResearchMaterial”.Eachpreviousversionofthe
foldercontentswillhavethedatethesnapshotwastakendisplayednexttoitandcontains
previous versions of the entire contents of the folder. The user can browse a read‐only
versionofthecontentsofanypreviousversionbyusingthe“Open”button.Similarly,the
“Copy”buttonallowstheusertospecifyadestinationtostoreacopyoftheselected
previousversionandthe“Restore”buttonrestoresthepreviousversionandreplacesthe
currentversionofthefolder.

‐47‐
Figure7.7‐'RestorePreviousVersions'inAction
Vistauses15%oftheavailable diskspaceonavolumetostoreshadowcopies,although
thiscanbeadjustedusingthe
C:\Windows\System32\vssadmin.exetool.Oncethe15%of
reservedspacehasbeenusedup,oldershadowcopiesaredeletedtomakespace53.The
datafortheshadowcopiesisstoredintheSystemVolumeInformationfolder.Researchers
fromCranfieldUniversityconductedexperimentationwiththeshadowcopycontainerfiles
14inthehopeofcreatingatooltoextracttheshadowcopies.Whilethistoolisstillin
development,theyhavereportedsuccessinviewingshadowcopiesofasuspectsystemby
bootinganimageofthesystemusingVMwareandthemethodsdescribedin54.
AsshadowcopiesaremadebydefaultonVistamachines,theymay provetobeof great
evidentiaryvalue.Iftheinvestigatorbelievescertainfiles/folderswerepresentonadrive
butdoesnotknowtheirpreviouslocation,theycansimplyuse“restorepreviousversions”
on the entire suspect volume. Thiswillthenshowanyshadowcopies that have been
createdofthevolume and theinvestigatorcannavigatethroughtheolderversionofthe
filesystemandevenperformsearches.
‐48‐
Itwasmentionedatthe beginningofthissectionthat“restore previousversions”isonly
availableintheBusiness,Enterprise,andUltimateeditionsofVista.However,usersofthe
HomeBasicandHomePremiumversionshavetheoptionofusingtheWindowsAnytime
UpgradetooltoupgradetoVistaUltimate.Userswhohavechosenthisupgradepathhave
found that once they have upgraded, Ultimate will let them restore previous files from
snapshotstakenwhiletheywererunningtheirHomeBasicorHomePremiuminstallations
55. While these editions of Vista do not provide the front‐end for restoring previous
versionsoffiles,alloftheworkoftakingsnapshotsofthevolumeisstillhappeninginthe
background.
Forthisreport,anumberoftestcasesweresetupinordertoevaluateVista’sability at
restoringfiles.ItwasfoundthatVistacanrestorepreviousversions of files and folders
evenifthefileshavebeendeletedandtherecyclebinemptied.Inaddition,SDeletev1.51
56byMarkRussinovichandEraserv5.8257wereusedto“securely”eraseanumberof
filesfromtheVistatestmachine.SDeletewasusedtoperforma20‐passoverwriteofone
setoftestfilesandEraserwasusedtoperforma35‐passGutmann58methodoverwrite
of another set of test files. Both sets of test files were then successfully recovered using
“restorepreviousversions”.
Investigators can use the
vssadmintoolC:\Windows\System32\vssadmin.exe to obtain
information about the shadow copiesfor a volume. One of the most useful commands is
vssadmin list shadowswhichshowsallvolumesnapshotsonasystemanddisplayshow
farbackthesnapshotsforeachvolumego.Forfulldetailssee59.
While the current investigation technique of restoring previous versions using a virtual
machineisnotideal,itdoesprovideexaminerswithavaluablesourceofevidencewhich
wouldnotbeavailableinWindowsXP.Iftheforensicresearchcommunity manages to
produceatoolthatcanrestorepreviousversionsoffileswithoutbootingthesuspectimage
onavirtualmachine,evidenceof this nature may open investigative avenues in cases
whichwouldhaveotherwiseproducednoresults.
‐49‐
7.2 – Other Vista Backup Options
TheBusiness,Enterprise,andUltimateeditionsofVistaallowuserstoaccesstoWindows
CompletePCBackup.Thiscreatesacompleteblock‐levelcopyofthevolumewhichtheuser
canlaterusetorestoretheirentiresystem.Backupsaresavedinvirtualharddrive
.vhd
formatandcaneitherbesavedtoanotherharddiskorsplitbetweenmultipleDVDs.These
.
vhdimagescanlaterbeusedtorestoreaconfigurationandcanalsobemountedinVirtual
PC200760orbeconvertedforuseinVMware.Investigatorsshouldalsobeawarethat
allversionsofVistaexceptforHomeBasicallowuserstoperformscheduledfilebackups
to network locations. Although most previous versions of Windows allowed a user to
manuallybackupfilestoanetworkedlocation,theautomationoftheprocessmayleadto
anincreaseinthenumberofhomeuserstransferringfilestonetworkdevices.

‐50‐
Chapter 8
Windows Mail
ThischapterdiscussestheWindowsMailemailandnewsgroupclientforVista.Itstartsby
givingabriefoverviewofWindowsMailanditspredecessorOutlookExpress.Thechapter
thendetailsthemethodsusedforstoringemailaccounts,emailfiles,newsgroupaccounts,
andnewsgroupposts.
8.1 – Windows Mail and Outlook Express
WindowsMailisanemailandnewsgroupclientincludedinallversionsofVista.Itisvery
similarinbothappearanceandfunctionalitytoOutlookExpresswhichwasincludedin
previous versions of Windows. Each mail folder in Outlook Expresshadacorresponding
.dbxthatheldallofthemessagesforthatfolder.Forensicanalysisofthesefilestypically
involvedtheuseofthird‐partytoolstoextracttheindividualemailfiles,orsimply
importing the
.dbx files to another Outlook Express configuration. Windows Mail has
discardedthe
.dbxcontainerformatandnowsimplystoresemailmessagesasindividual
files.
8.2 – Windows Mail Files and Folders
EachemailaccountaddedtoWindowsMailwillhaveitsownaccountfoldercreated.These
folders are created in
C:\Users\<username>\AppData\Local\Microsoft\Windows Mail\
bydefaultalthoughthislocationcanbechangedviatheregistry.Bydefault,Vistacreates
a
Local Foldersaccountfolderwhichholdsthemessagesandaccountinformationforany
POP3accounts61.Eachnon‐POP3emailaccounttheuseraddswillhaveitsownfolder
created.Thedefaultnamingconventionistonamethefolderaftertheincomingmailserver
e.g.
imaphost.cis.strath.ac.uk)althoughtheusercanchangethislater.Eachaccount
folderwillthencontainthefollowing:
• A
.oeaccountfilewhichcontainstheaccountpropertydata
‐51‐
• Anumberofmailfolderse.g.Inbox,Outbox,Sent Items
8.2.1 – Account Property Data (.oeaccount) Files
Account details are held in XML formatandarestoredinfilenameswiththeformat
account{XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX}.oeaccount where each Xisa
hexadecimaldigit.Acomprehensivelistofthedatafieldscontainedintheaccountproperty
filesisavailablefromreference61.Investigatorsshouldbe aware that there are three
accountdatafilessetupbydefaultonaVistasystem.ThefirsttwoareusedforActive
Directory and the VeriSign Internet Directory Service. They arelocatedin
C:\Users\<username>\AppData\Local\Microsoft\Windows Mail\andhavesizesof1,736
bytesand1,508bytesrespectively.Thethirdfileis672bytes inlengthandis locatedin
C:\Users\<username>\AppData\Local\Microsoft\Windows Mail\Microsoft Communities\.
8.2.2 – Mail Folders
Eachemailfoldercontainsawinmail.folfilewhichtracksthefolderlocationandtheemail
itemsinthefolder62.Anyotherfilespresentinthefolderwillbetheconstituent
.eml
emailfiles.
8.2.3 – Email (.eml) Files
Email filenames take the format XXXXXXXX-XXXXXXXX.emlwhereeachXisahexadecimal
digit.Theemaildataisstoreasplaintextandcanbeviewedwithanytexteditor.The
.eml
files contain the full header of the email, the body of the message, and any attachments.
Attachmentscaneitherbeextractedfromthe
.emlfilesoraforensicworkstationrunning
WindowsMailcanbeusedtoopenthe
.emlfile and view the attachments.Investigators
shouldbeawarethatWindowsMailsupportsencryptionofoutgoing mail using digital
signatures 63. Email messages which are sent with encryption enabled are encrypted
beforebeingplacedintheOutboxthereforethebodyoftheemailwillbeunreadablebut
theemailheaderisstillinplaintext11.
‐52‐
8.3 – Windows Contacts
ContactsforauserarecontainedintheC:\Users\<username>\Contacts\ folder.Contact
filestakethefilenameformatof
<contact name>.contactwhere<contact name>isthe
contact’sfullnameandaresimpleXMLfilescontaininginformationaboutthecontact.The
fulllistofpropertiesthatcanbeaddedtoacontactfilearelistedin64.TheContacts
folderisalsousedtostorethelistofcontactsforanyWindows Live accounts thathave
beenaccessedfromtheuser’saccounte.g.usingWindowsLiveMessenger.Thecontacts
foraWindowsLiveaccountareplacedintoafoldernamedaftertheaccount.WindowsLive
Messenger encrypts the contacts by default and stores them in files with the filename
format
XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX.WindowsLiveContactwhereeachXisa
hexadecimaldigit.ThefolderfortheWindowsLiveaccountwillalsocontainafilenamed
contactcoll.cache.Thisisacacheofallthecontactsassociatedwiththeaccount but is
also encrypted by default. These files can be unencrypted by disabling encryption of
contactsviatheoptionsinWindowsLiveMessenger.Duringtestingitwasobservedthat
evenifencryptionisturnedbackon,plaintextcopiesofthecontactnamesareavailable
from the
contactcoll.cache file. Any further contacts added when encryption is re‐
enabledareappendedasencryptedentriesto
contactcoll.cachewhiletheoldercontacts
remaininplaintext.
8.4 – Windows Mail Log File
WindowsMailmaintainsalogfilerelatingtosentandreceivedemail.Itiscontainedinthe
file
C:\Users\<username>\AppData\Local\Microsoft\Windows Mail\edb.log.Byopening
the file with a hex editor, email headers for a number of sent and received emails were
clearly visible. A test set of 24 emails was used to send and receive email to/from an
account.Ofthetestset,headerinformationfor20oftheemailswasretrievedfromthelog
fileincludingsubject,datesend,sender,andrecipient.Examinersshouldnotethatoutgoing
email logged in the file will reference the sender by the
.oeaccount filename for the
account,ratherthantheemailaddress.Theinformationinthislogfilepersistsevenafter
users clear all email folders through Windows Mail Tools‐Options‐Advanced Tab‐
‐53‐
’Maintenance’‐’Clean Up Now’‐Reset. Testing showed that as expected ‘deleted’
emailcanalsoberecoveredusingRestorePreviousVersionsseeSection7.1.
8.5 – Newsgroups
Thestoragesystemfornewsgroupaccountsismuchthesameasforemailaccounts.They
reside in
C:\Users\<username>\AppData\Local\Microsoft\Windows Mail\asnewsgroup
account folders named after the news server e.g.
nntphost.cis.strath.ac.uk.The
newsgroup account folders then contain an
.oeaccountfileforholdingtheaccount
properties. They will also contain a number of subfolders whicharenamedafterany
newsgroupswhichhavebeensubscribedtounderthatnewsgroupaccount.These,inturn,
containa
winmail.folfilediscussedearlierandindividualfilesforeachpostwhichtake
the filename format
XXXXXXXX-XXXXXXXX.nwswhereeachX is a hexadecimal digit. The
headerandbodyinformationisstoredinplaintextandcanbeviewedwithatexteditor.

‐54‐
Chapter 9
Internet Explorer 7 for Vista
ThischapterprovidesinvestigatorswithanintroductiontoInternetExplorer7IE7for
VistaandhowitdiffersfromitsXPcounterpart.Itthendiscussesthenewfoldersusedin
IE7andtheupdatedlocationsfortheindex.datfiles.Thechapterfinishesbydescribing
passwordstorageandthenewfeaturesfordeletingbrowsinghistory.
9.1 – Introductory Note
InternetExplorer7isthewebbrowserincludedwithWindowsVista.Whileinvestigators
mayhavecomeacrossIE7whenexaminingWindowsXPmachines,theyshouldrealisethat
theversionincludedinVistaissignificantlydifferent.Thetwoarebuiltfromthesamecode
base65andlookpracticallyidentical,buttheaddedsecurity features in IE7 for Vista
makeitconsiderablydifferentfromaninvestigativepointofview.
9.2 – Protected Mode for IE7
All versions of Windows Vista come with the Internet Explorer 7IE7webbrowser.
Microsoftiswellawarethatthereisahighersecurityriskassociatedwithwebbrowsers
thanthereiswiththemajorityofWindowsapplicationsavailable to end‐users. For this
reason, IE7 for Vista uses a defence‐in‐depth approach to security known as Protected
Mode,withmultiplelayersofdefenceplacedthroughoutthesystem. Protected Mode
utilisesthreenewtechnologiesfromtheWindowsVistasecuritymodel66:
• UserAccountControlUAC–Aleastprivilegetoaccesscontrolwherealluserson
thesystem run as astandard user. If ataskrequires higher privileges, the useris
promptedwithanelevationrequestthatgivestemporaryrightstoperformthetask
ontheconditionthattheuser’saccounthasthenecessarycredentialsseeChapter2
forfulldetails.
‐55‐
• MandatoryIntegrity Control MIC–Amodelto preventlowerintegrityprocesses
fromperformingwritesordeletesWindowssecurableobjects67suchasfilesor
registrykeys.Vistausesfourprimaryintegritylevels:Low,Medium, High, and
System. Processes are assigned an integrity level and can only access securable
objectsthathaveanequalorlowerintegritylevel.
• UserInterfacePrivilegeIsolationUIPI–Usedtoblocklowerintegrityprocesses
fromaccessinghigherintegrityprocesses.
IE7for Vistarunsin ProtectedModebydefault,duringwhichtimetheInternetExplorer
process
iexplore.exerunsasalowintegrityprocess.Anyadd‐insavailableforIE7such
astoolbarsandActiveXcontrolsallrunwithintheIEprocessandthereforealsorunasLow
integrity68.Asaresult,IE7anditsadd‐insrunninginProtectedModecanonlywriteto
lowintegritylocations.Therefore,insteadofIE7usingsingle folders for each of cache,
cookies,history,andtempfiles,apairoffoldersisused.EachhasafolderforwhenIE7is
runningoutsideofProtectedModewhich,inturn,holdsa
Lowsubfoldertoholdcontentfor
whenIE7isrunninginProtectedMode.Thelocationsofthesefoldersareshownbelow:
• Cache:
C:\Users\<username>\AppData\Local\Microsoft\Windows\Temporary Internet
Files\
C:\Users\<username>\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low
• Cookies:
C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Cookies\
C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Cookies\Low
• History:
C:\Users\<username>\AppData\Local\Microsoft\Windows\History\
C:\Users\<username>\AppData\Local\Microsoft\Windows\History\Low
• Temp:
C:\Users\<username>\AppData\Local\Temp\
C:\Users\<username>\AppData\Local\Temp\Low

‐56‐
Another consequence of running in Protected Mode is that Internet Explorer extensions
attemptingtowritetosystemlocationssuchas
Program FilesandtheHKCUregistryhive
areautomaticallyredirectedtothefollowinglowintegritylocations69:
• Virtualizedfolder:
C:\Users\<username>\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Virtualized
• Virtualizedregistrykey:
HKCU\Software\Microsoft\Internet Explorer\InternetRegistry
Thefavoritesfolderdoesnotrequirealowintegrityversion.Itresidesin
C:\Users\<username>\Favorites.
9.3– Internet Explorer 7 Cache and index.dat Files
IE7appearstocachewebcontentinthesamemannerasInternetExplorer6.Temporary
Internet Files
containsaContent.IE5folderwhich,inturn,containsfoldersofthe
format
XXXXXXXX where each Xisanalphanumericcharacternote:rememberthatthere
willalsobetheLowversionofthecache.Thesefoldersthencontainanywebcontentthat
hasbeencachedbyIE7.
IE7 also uses the same format for index.dat files and they are still readable using
applicationsthatreadIE6index.datfiles.Thefollowingisalistofindex.datfilelocationson
atypicalVistamachineandabriefdescriptionofeachdescriptionsforeachindexfileare
basedoninformationfrom70:
C:\Users\<username>\AppData\Local\Microsoft\Feeds Cache
• Holds an index of RSS feeds added to IE7.
C:\Users\<username>\AppData\Local\Microsoft\Windows\History\History.IE5
• Contains a list of the URLs that have been clicked when browsing. Allows IE7 to auto-
complete URLs and mark links which have been visited in a different colour.

‐57‐
C:\Users\<username>\AppData\Local\Microsoft\Windows\History\Low\History.IE5
• As above except holds data when IE7 is in Protected Mode.
C:\Users\<username>\AppData\Local\Microsoft\Windows\History\History.IE5\MSHis
t01<date><date>
• These are history containers used for the different range dates that IE7 displays (e.g.
today, yesterday, last week etc). The first
<date> field specifies the start date for that
particular history container and the second
<date> filed specifies the end date
C:\Users\<username>\AppData\Local\Microsoft\Windows\History\Low\History.IE5\M
SHist01<date><date>
• As above except holds data when IE7 is in Protected Mode.
C:\Users\<username>\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Content.IE5
• URLs of web content such as pages, images, and JavaScript are cacheable are placed into
this index file until they expire.
C:\Users\<username>\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Low\Content.IE5
• As above except holds data when IE7 is in Protected Mode.
C:\Users\<username>\AppData\Roaming\Microsoft\Internet Explorer\UserData\
• Holds URLs for userData entries which are essentially sophisticated cookies. See [71] for
more details of userData objects. (Note: This folder and its low-integrity counterpart will
only be created when IE7 first encounters a web page utilising userData objects).
C:\Users\<username>\AppData\Roaming\Microsoft\Internet Explorer\UserData\Low
• As above except holds data when IE7 is in Protected Mode.

‐58‐
C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Cookies
• Used to map cookie URLs to individual cookie files.
C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Cookies\Low
• As above except holds data when IE7 is in Protected Mode.
9.4– Passwords
InternetExplorer7includespasswordmanagementfacilitiesinordertoreducetheburden
oftryingtoremembernumerouspasswords.Inadditiontohelpingtheuser,thesecanalso
bevaluableforinvestigators.ComprehensivedetailsofthestoragemechanismsusedinIE7
areavailablefrom8.
9.4.1– Internet Credentials
Theuserwillbepromptedfortheirinternetcredentialspasswordwhenevertheyattempt
toaccesscertainwebsitesthatrequirethe
wininet.dlllibrary72.Thiswillautomatically
launchtheCredentialManagerUserInterfaceseeFigure9.1whichpromptstheuserfor
their username and password. The password will be saved in an encrypted file under
C:\Users\<username>\AppData\Roaming\Microsoft\Credentials assuming “Remember
mypassword”isticked.
Figure9.1‐PromptforInternetCredentials
‐59‐
9.4.2– AutoComplete Information
The AutoComplete of Internet Explorer is intended to save userstimebyrecording
information the user types to the browser such as website addresses, form information
including username/password combinations, and search queries. Previous versions of
InternetExplorerencryptedAutoCompletedatabyusingtheWindowsProtectedStorage
APIPStore73.ThedataisencryptedusingtheTripleDESalgorithmfromthe
CryptoAPI
74.Althoughthisalgorithmisconsideredtobesecure,accesstotheencrypteddataistied
to a user’s Windows
logon credential
75. In a typical system, this is provided by
calculatingthehashof theuser’spassword.Once the useris loggedin, any programcan
accesstheunencrypteddatabyusingthePStore
API.Thisposesaserioussecurityriskand
soMicrosofthasoptedtonowstoreencryptedAutoCompletedatausingtheData
ProtectionAPIDPAPI76.
DPAPI provides software developers with OS‐level data protection services. This allows
developers to create applications that can secure data by simply using function calls to
DPAPI rather than having to write their own application‐specific cryptographic code. As
with PStore, thepassword used in the encryption/decryption processis the user’s logon
credential. However, DPAPI allows applications to use an additional password when
protectingdata,therebyovercomingthevulnerabilitiesofPStorebyhinderingtheabilityof
oneapplicationtocompromiseanotherapplication’sencryptionkey.
AllofthedatastoredforAutoCompletefieldsi.e.AutoCompletestringsfordataformsis
stored in the
HKCU\Software\Microsoft\Internet Explorer\IntelliForms\Storage1
registrykey.ItisheldasanencryptedlistofHTMLformfieldnamesandthecorresponding
datatheuserenteredinthatfield.Unfortunately,thenameorURLoftheWebpageisnot
cached. For example, if a user visits
http://www.google.co.uk/ and types the search
query “TEST1”, Internet Explorer will only cache the AutoCompleteentry“TEST1”
assuming the corresponding AutoComplete option is enabled as wellastheformfield
name“q”asthisistheformfieldnameassignedtotheinputboxontheGoogle
homepage.
‐60‐
AutoCompleteforstoringwebsitepasswordsworksinasimilarfashionasitdoesforfields.
The main difference is that each password is linked to a specific webpage whereas
AutoCompletedataforfieldsisjustlinkedtoaformfieldname.Theencrypteddataisheld
in the
HKCU\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 registry
key.TheencryptionanddecryptionprocessforAutoCompletepasswords is as follows
72:
Encryption:
1. SavetheURLofthewebpage.Thisisthenusedastheencryptionkey:
EncryptionKey = URL
2. Calculatethehashoftheencryptionkeyandstorethisastherecordkey:
RecordKey = SHA(EncryptionKey)
3. Calculatethechecksumfor
RecordKeytoensureintegrity:
RecordKeyCRC = CRC(RecordKey)
4. Encryptthedatapasswordsusingtheencryptionkey:
EncryptedData = DPAPI_Encrypt(Data, EncryptionKey)
5. Save
RecordKeyCRC,RecordKey,andEncryptedDataintheregistry.
6. Discard
EncryptionKey.
Decryption:
1. Whentheoriginalpageisopen,useitsURLshouldmatchoriginal
EncryptionKey
tocalculatetherecordkey:
RecordKey = SHA(EncryptionKey)
2. Scanthroughthelistofrecordkeysintheregistrytryingtofind
RecordKey
3. If
RecordKeyisfoundintheregistrylist,decryptthedatastoredalongsideitusing
EncryptionKey:
Data = DPAPI_Decrypt(EncryptedData, EncryptionKey)
From the decryption process outlined above, it should be obviousthatwithoutthe
appropriateURL,apasswordstoredinthe
Storage2 registry key cannot be decrypted.
‐61‐
SoftwarethatautomatesthedecryptionoftheseregistrykeyssuchasPasscapeInternet
ExplorerPasswordRecovery77worksbyusingtheURLthatisstoredinthebrowser
history. If the history has been cleared, the only way an examiner can retrieve the
passwordisbymanuallytryingURLsinthehopethattheyfindthecorrectonetounlock
thedata.
9.5 – Deleting Browsing History
Bydefault,InternetExplorer7uses50mbforthediskcacheandkeepsvisitedpagesinthe
historyfor20days.However,ithasnowmadetheprocessofdeletingthebrowserhistory
mucheasier.Theusernowusesthe“DeleteBrowsingHistory”optionfromtheToolsdrop‐
downmenuontheIE7toolbar.Thisopensadialogwheretheuser can either clear
individualcomponentsofthebrowsinghistoryTemporaryInternetFiles,Cookies,History,
FormData,Passwordsortheyhavea“DeleteAll”option.Thiswilldeleteallthedata
mentioned above but also now wipes the
index.dat files. Instead of simply deleting the
oldfile,itisoverwrittenwithblankspaces.Usingahexeditor,theversioninformationfor
eachindexfilewasstillvisible“ClientUrlCacheMMFVer5.2”andtherestofthefilewas
filledwith
0x20.

‐62‐
Chapter 10
Additional Points of Interest
ThischapterexplainsavarietyoffeaturesinVistathatmayhave significance during an
investigation.
10.1 – The Recycle Bin
TheXPRecycleBinwasheldintheRECYCLERfolderattherootofadrive.Thisheldanyfiles
thathadbeendeletedandalsocontainedan
INFO2thatmappedthefilesintheRECYCLER
foldertotheiroriginalpathcomprehensivecoverageofthissubjectisavailablefrom78.
Vista’sRecycleBinisheldinthe
$Recycle.Binfolderattherootofadrive.Thisfolderthen
containssubfoldersnamedaftertheSIDoftheuserwhodeletedthefile.Thesesubfolders
thencontainanyfilesthathavebeendeletedbytheuser.
Vistanolongerusesan
INFO2filetotracktheoriginallocationoffiles.Instead,whenafile
orfolderisdeletedi.e.movedtotheRecycleBintwofilesarecreated.Thefirstfilewillbe
of the form
$I<fileID>.<ext>where<fileID> is a unique six‐character alphanumeric
string.
<ext> istheoriginalextensionofthefilethathasbeendeletednoextensionifa
folder was deleted. These
$I filescontainan8‐byteFILETIMEstructureatoffset0x10
thatholdsthetimethefile/folderwasdeleted.Theythencontainthefullpathandfilename
oftheoriginalfile/folderatoffset
0x18.Eachofthese$Ientrieswillhaveacorresponding
fileorfolderpresentalongsidethem.Forfoldersthathavebeendeleted,afolderiscreated
named
$R<fileID>where<fileID>willmatchthe<fileID>usedinthecorresponding$I
file.Anycontentsofthedeletedfolderaremovedtothe
$Rfolderandretaintheiroriginal
names.FilesthathavebeenmovedtotheRecycleBinarerenamed
$R<fileID>.<ext>
where
<fileID>and<ext>willmatchthoseusedinthecorresponding$Ifile.As$Rfiles
arejusttheoriginalfileswithadifferentname,theycontainalltheactualcontentofthe
originalfile.
‐63‐
10.2 – Acquisition of Physical Memory
AcquisitionofphysicalmemoryinWindowsXPinvolvesusingatoolsuchasDDfromthe
ForensicAcquisitionUtilities79.Itreliesontakingadump of the physical memory by
using the
\Device\PhysicalMemory see 80 object to access physical memory from a
user‐mode application. This is not possible in Vista as access to the
\Device\PhysicalMemoryobjecthasbeenrestrictedtokernel‐modedrivers80.Physical
memory acquisition in VistamaystillbepossibleinsystemsthatsupporteitherUSBor
FireWire.BoththeUSBandFireWire specifications allowaccess to physicalmemory via
Direct Memory Access DMA. This has been successfully demoed using FireWire 81
whereaccesstothephysicalmemoryisinitiatedfromthedeviceside.AstheaccessisDMA,
thedevicee.g.aLinuxmachinecandirectlyaccessthememoryonthehostmachineand
circumventanyOSprotectionintheprocess82.
10.3 – ReadyBoost
ReadyBoostisatechnologyavailableinVistathatisusedforcachingdiskdata.Theideais
that an external USB flash device is used to supplement the mainmemoryofaPCand
reducetheneedtoaccesstheharddiskforrandomI/Oreads.Thisinitiallyseemslikean
interestingprospectfromaninvestigativepointofview.TheproblemisthatVistaencrypts
thedatawrittentotheUSBdevicewithAES‐128usingaper‐bootencryptionkey49.This
effectivelymakesameaningfulexaminationofthedeviceimpossible.
10.4 – Transactional NTFS and Transactional Registry
TransactionalNTFSTxFandTransactionalRegistyTxRaretwofeaturesinVistawhich
arebuiltontopoftheVistaKernelTransactionManagerKTM83. The Microsoft
definitionofTxFis“TransactionalNTFSallowsanapplicationtogroupmultipleoperations
onmultiplefilesasasingleunit”84.Basicallyitisamethod of ensuring a set of file
operations occur as required i.e. as a set or are rolled back. TxR is a similar concept
except it ensures a transaction for a set of registry operations occurs properly. These
featureswillbeusefulwhenappliedtoscenariossuchassoftware upgrades, but at the
momenttheydonothavemuchsignificancefromaforensicperspective.
‐64‐
10.5 – Disk Defragmenter
ThediskdefragmenterinVistaworksinmuchthesamewayasitdidinXPexceptwitha
simplifiedGUI.Themainconcernforinvestigatorsisthat,bydefault,thedefragmenteris
scheduledtorunautomaticallyat 1am every Wednesday on Vista systems. Scheduled
defragmentation that is enabled by default has obvious implications with regards to
recoveryofdeletedfiles.RecoveryoffilesfromshadowcopiesseeSection7.1maystillbe
possible although defragmentation is known to affect shadow copies in systems with a
cluster size of less than 16KB 85. Examiners should be aware that the scheduled disk
defragmenteroperatesonallvolumes86.

‐65‐
Chapter 11
Conclusion
This report has attempted to detail some of the issues surrounding the forensic
investigationoftheWindowsVistaplatform.Muchofthecontent is the result of the
research conducted at QinetiQ. In addition to this content, information gathered from a
numberofothersources,includingthepapersmentionedinSection1.3,hasbeenverified
anddocumented.
Despiteinitialworryfromtheforensiccommunity,WindowsVistadoesnotappeartobe
significantlydifferenttoWindowsXPintermsofperformingaforensicinvestigation.The
BitLockerencryptionsystemwillcertainlystarttobeencounteredmorefrequentlyinlive
response situations and this may lead to an emphasis on live analysisofamachine.The
othermajorchangeinVistathatmaychangepartofaninvestigativestrategyistheabsence
of last access times. Traditional means of creating a profile of file activity based on last
access times will therefore be made redundant and examiners will have to utilise other
methods of investigation. The other changes documented in the report will simply
necessitateaslightre‐educationonaparticularaspectoftheoperatingsystemor,whatis
probably the more likely scenario, the tweaking of a particular tool that automates that
partoftheinvestigation.
WhilethelastparagraphhasfocusedonsomeofthechallengescreatedbyVista,thereare
otherpointsthatworkinanexaminer’sfavour.Forinstance,themovingofthethumbnail
cachetoacentralisedlocationshouldleadtoanincreaseintheamountofevidencethat
canbeaccumulatedfromthumbnails.Themajornewfeaturethatworksinanexaminer’s
favouristheVolumeShadowCopymaterialthatresidesonVistavolumes.Thiscouldprove
tobeoneofthemostsignificantfeaturesusedinaninvestigationofaVistaMachine.
Thereareanumberofpointscoveredinthereportbutitisbynomeansanexhaustivelook
attheforensicissuessurroundingWindowsVista.Someofthepoints, in particular
BitLocker and Volume Shadow Copy, would merit an entire report alone. Due to time
‐66‐
constraints,an exhaustive look was not possible. Instead, the reporthasshedsomenew
lighton Vistaandattemptedtocollateinformationscatteredamongstanumberofother
sources.Hopefullytheinformationcanbeputtouseinaworkingforensiclabandperhaps
tocontributetofurtherresearch.

‐67‐
Chapter 12
Suggestions for Further Work
Asexplainedintheconclusion,thereisalotofresearchstilltobeconductedonWindows
Vista.Therearealreadyattemptsbeingmadeatcircumventingparts of the BitLocker
encryptionseeSection4.13anditwillbeinterestingtoseehowthesedevelop.Withthe
currentsituationofBitLockerneverhavingbeensuccessfullyattacked,anemphasiswillbe
placeonliveresponseofsystemsrunningBitLocker.Liveanalysisofmachineshasalways
beenapointofcontentionindigitalforensics.However,asdiskencryptionbecomesmore
prevalent the issue of live analysisbecomesmoreimportantasitmaywellbetheonly
opportunity to gather evidence from a system. The forensic community needs to
collectivelyworktowardsanagreedstrategytobeusedinlivesystemanalysisscenariosas
attemptstobreaktheencryptionsystemsmayultimatelyprovefutile.
Thedevelopmentofatoolthatcouldrestorepreviousversionsoffilesusingshadowcopies
would be a major coup for the forensic community. This would open up a wealth of
information residing on a volume that could be of great evidentiaryvalue.Thecurrent
techniqueinvolvesrunninglivesystemsandonlyworkswithcertaineditionsofVistasee
Section7.1whichisfarfromideal.
AnothermajorlimitationwithWindowsVistaistheinabilitytotakeadumpofthephysical
memoryusingtraditionaltoolsseeSection10.2.ThehardwarerequirementsofVistawill
belikelytoforcemanyusersintoupgradingtheircomputerswhichmayleadtoarisein
the number of FireWire‐enabled computers encountered during live incident response.
Thisprovidesaviableavenuefortheacquisitionofphysicalmemoryalthoughthiscannot
bereliedonasthesolemethodofdoingso.Acquisitionofmemory based on a software
approachwouldbemoredesirableinthesensethatitcouldbemorewidelyutilised.Even
betterwouldbeareliableDMA‐basedmethodusingUSBasthiswould require no in‐
memoryartifact.
‐68‐
Research involving the forensic investigation of Vista systems is still in its infancy.
However,theforensicresearchcommunityhasaloyalanddedicatedcorewhichshould,in
time,overcomethemajorityofissuesfacingthemregardingtheexaminationofVista.

‐69‐
Appendix A
References
Thissectioncontainsthereferencesusedthroughoutthereport.
1. Software:VMwareWorkstationVersion6.
VMwareInc
.Accessed01‐09‐2007
http://www.vmware.com/products/ws/
2. Software:WinHexv14.3.
X‐WaysSoftwareTechnology
.Accessed01‐09‐2007
http://www.x‐ways.net/winhex/
3. Software:Notepad.Accessed01‐09‐2007
http://notepad‐plus.sourceforge.net/uk/about.php
4. Software:ProcessMonitorv1.22.MarkRussinovichandBryceCogswell.Accessed
01‐09‐2007
http://www.microsoft.com/technet/sysinternals/utilities/processmonitor.mspx
5. Software:Regshot.Accessed01‐09‐2007
http://regshot.blog.googlepages.com/regshot
6. Software:FTKImager.
AccessData.
Accessed01‐09‐2007
http://www.accessdata.com/catalog/partdetail.aspx?partno11300
7. JamieMorris,“NotesonVistaForensics,PartOne”.
SecurityFocusArticle
.March
2007.Accessed01‐09‐2007
http://www.securityfocus.com/infocus/1889/2
8. JamieMorris,“NotesonVistaForensics,PartTwo”.
SecurityFocusArticle
.April
2007.Accessed01‐09‐2007
http://www.securityfocus.com/infocus/1890
9. Website:ForensicFocus.Accessed01‐09‐2007
http://www.forensicfocus.com/

‐70‐
10. Website:GuidanceSoftwareInc.Accessed01‐09‐2007
http://www.guidancesoftware.com/
11. LanceMueller,“FirstLooks:BasicInvestigationsofWindowsVista”.
Computerand
EnterpriseInvestigationsConference2007
.May2007.Accessed01‐09‐2007
http://www.lancemueller.com/vistaceic2007.ppt
12. TJCampana,“MicrosoftWindowsVistaForensicJumpstart”,
TechnoSecurity2007
Presentation
.June2007.Accessed01‐09‐2007
http://www.techsec.com/TS‐2007‐PDF/Mo%20T6‐1.pdf
13. JeanGautier,“BitLockerDriveEncryption”.MicrosoftLawEnforcement
Presentation.July2007.Accessed01‐09‐2007
http://download.microsoft.com/documents/uk/business/BitLocker%20Forensics
%20UK%20‐%20Final.pdf
14. ChrisHargreavesandHowardChivers,“PotentialImpactsofWindowsVistaon
DigitalInvestigations”.
AdvancesinComputerSecurityandForensicsACSF2007
Conference
.April,2007.
15. Microsoft,“UserAccountControlOverview”.
MicrosoftTechNetArticle
.February
2006.Accessed01‐09‐2007
http://technet.microsoft.com/en‐us/windowsvista/aa906021.aspx
16. Microsoft,“HowWindowsVistaHelpsProtectComputersfromMalware”.
Microsoft
TechNetArticle
,September2006.Accessed01‐09‐2007
http://technet.microsoft.com/en‐us/windowsvista/aa940967.aspx
17. WesnerMoise,“SymbolicLinksinVista”.
SmartSoftwareBlog
.October2006.
Accessed01‐09‐2007
http://wesnerm.blogs.com/net_undocumented/2006/10/symbolic_links_.html
18. MicrosoftMSDN,“TheWindowsVistaandWindowsServer2008DeveloperStory:
ApplicationCompatibilityCookbook”.
MSDNTechnicalArticle
.July2006.Accessed
01‐09‐2007
http://msdn2.microsoft.com/En‐US/library/aa480152.aspx

‐71‐
19. BBCNews,“Q&A:TKMaxxcreditcardfraud”.March2007.Accessed23/08/2007
http://news.bbc.co.uk/1/hi/business/6509993.stm
20. GCNNews,“VADataFilesonMillionsofVeteransStolen”.May2006.Accessed
23/08/2007
http://www.gcn.com/online/vol1_no1/40840‐1.html
21. Website:PrivacyRightsClearinghouse.Accessed23/08/2007
http://www.privacyrights.org/
22. Software:PetterNordahl‐Hagen.TheOfflineNTPasswordEditor.Accessed01‐09‐
2007
http://home.eunet.no/pnordahl/ntpasswd/
23. Software:ObjectifSécurité..Ophcrackv2.4.1.Accessed01‐09‐2007
http://ophcrack.sourceforge.net/
24. Microsoft,“ErrormessagewhenyoutrytostartaWindowsVista‐basedcomputer
thatisconfiguredtouseBitLocker:“ThePINhasbeenenteredincorrectlytoomany
times”.
MicrosoftKBArticle
.November2006.Accessed01‐09‐2007
http://support.microsoft.com/kb/926187
25. NielsFerguson,“AES‐CBCElephantDiffuser.ADiskEncryptionAlgorithmfor
WindowsVista”.August2006.Accessed01‐09‐2007
http://download.microsoft.com/download/0/2/3/0238acaf‐d3bf‐4a6d‐b3d6‐
0a0be4bbb36e/BitLockerCipher200608.pdf
26. NationalInstituteofStandardsandTechnology,“AnnouncingtheAdvanced
EncryptionStandardAES”.
FederalInformationProcessingStandardsPublication
197
.November2001.Accessed01‐09‐2007
http://csrc.nist.gov/publications/fips/fips197/fips‐197.pdf
27. ByronHynes,“KeystoProtectingDatawithBitLockerDriveEncryption”.
Microsoft
TechNetArticle
.June2007.Accessed01‐09‐2007
http://www.microsoft.com/technet/technetmag/issues/2007/06/BitLocker/
28. ShonEizenhoefer,“BitLockerDriveEncryption–HardwareEnhancedData
Protection”.
MicrosoftWinHEC2006Presentation
.Accessed01‐09‐2007
http://download.microsoft.com/download/5/b/9/5b97017b‐e28a‐4bae‐ba48‐
174cf47d23cd/CPA064_WH06.ppt

‐72‐
29. Microsoft,“BitLockerDriveEncryption:Scenarios,UserExperience,andFlow”,May
2006.Accessed01‐09‐2007
http://download.microsoft.com/download/a/f/7/af7777e5‐7dcd‐4800‐8a0a‐
b18336565f5b/BitLockerFlow.doc
30. JamieHunter,“DetectingBitLocker”.
MSDNSystemIntegrityTeamBlog
.October
2006.Accessed01‐09‐2007
http://blogs.msdn.com/si_team/archive/2006/10/26/detecting‐bitlocker.aspx
31. Microsoft,“ConfiguringActiveDirectorytoBackupWindowsBitLockerDrive
EncryptionandTrustedPlatformModuleRecoveryInformation”.
MicrosoftTechNet
Whitepaper
.December2006.Accessed01‐09‐2007
http://technet2.microsoft.com/WindowsVista/en/library/3dbad515‐5a32‐4330‐
ad6f‐d1fb6dfcdd411033.mspx
32. Microsoft,“WindowsMarketplace:DigitalLockerTour”.Accessed01‐09‐2007
http://www.windowsmarketplace.com/content.aspx?ctId302&tabid1
33. DouglasMacIver,“PenetrationTestingWindowsVistaBitLockerDriveEncryption”.
HackintheBoxPresentation
.September2006.Accessed01‐09‐2007
http://conference.hackinthebox.org/hitbsecconf2006kl/materials/DAY%202%20‐
%20Douglas%20MacIver%20‐%20Pentesting%20BitLocker.pdf
34. Website:NVLabs.Accessed01‐09‐2007
http://www.nvlabs.in/
35. NitinKumarandVipinKumar,“TPMkit:BreakingtheLegendofTrusted
ComputingTCTPMandVistaBitLocker”‐Abstract.May2007.Accessed01‐
09‐2007
http://seclists.org/dailydave/2007/q2/0102.html
36. DaringtonForbes,“OntheBlackPage:TPMkit”.June2007.Accessed01‐09‐2007
http://www.blackhat.com/html/bh‐blackpage/bh‐blackpage‐06292007.html
37. Website:“Thumbs.dbinimagingsystems”.
AllianceGroupUK
.Accessed01‐09‐
2007
http://www.alliancegroup.co.uk/thumbs.htm

‐73‐
38. DustinHurlbut,“ThumbsDBFilesForensicIssues”.
AccessDataTrainingDocument
.
2005.Accessed01‐09‐2007
http://www.accessdata.com/media/en_US/print/papers/wp.Thumbs_DB_Files.en_
us.pdf
39. Software:TheForensicToolkit.AccessData.Accessed01‐09‐2007
http://www.accessdata.com/catalog/partdetail.aspx?partno11000
40. MSDNLibraryEntry,“ThumbnailProviders”.Microsoft.2007.Accessed01‐09‐
2007
http://msdn2.microsoft.com/en‐us/library/aa969355.aspx
41. Microsoft,“FileTimes”.
MSDNArticle
.February2007.Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/ms724290.aspx
42. Microsoft,“Preventing‘LastAccess’Chatter”.
WindowsXPEmbeddedTeamBlog
.
February2006.Accessed01‐09‐2007
http://blogs.msdn.com/embedded/archive/2006/02/01/522053.aspx
43. Microsoft,“DisablingLastAccessTimeinWindowsVistatoImproveNTFS
Performance”.
MicrosoftTechNetFilingCabinetBlog
.November2006.Accessed
01‐09‐2007
http://blogs.technet.com/filecab/archive/2006/11/07/disabling‐last‐access‐time‐
in‐windows‐vista‐to‐improve‐ntfs‐performance.aspx
44. JeremyB.Smith,“YetAnotherMethodWindowsUsestoLogYourComputer
Activity”.Accessed01‐09‐2007
http://www.geocities.com/TimesSquare/Maze/1125/articles/explorer_spy.txt
45. Software:UserAssistv2.3.0.DidierStevens.Accessed01‐09‐2007
http://blog.didierstevens.com/programs/userassist/
46. Microsoft,“WindowsPCAccelerators”.
MicrosoftWhitepaper
.November2006.
Accessed01‐09‐2007

‐74‐
http://download.microsoft.com/download/9/c/5/9c5b2167‐8017‐4bae‐9fde‐
d599bac8184a/perfaccel.doc
47. Microsoft,“MeasuringPerformanceinWindowsVista”.
MicrosoftWhitepaper
.July
2007.Accessed01‐09‐2007
http://download.microsoft.com/download/9/c/5/9c5b2167‐8017‐4bae‐9fde‐
d599bac8184a/Vista_perf.doc
48. HarlanCarvey,“WhatisthePrefetcher”.
WindowsIncidentResponseBlog
.March
2005.Accessed01‐09‐2007
http://windowsir.blogspot.com/2005/03/what‐is‐prefetcher.html
49. MarkRussinovich,“InsidetheWindowsVistaKernel:Part2”.
MicrosoftTechNet
Article
.March2007.Accessed01‐09‐2007
http://www.microsoft.com/technet/technetmag/issues/2007/03/VistaKernel/
50. Microsoft,“PreviousVersionsofFiles:FrequentlyAskedQuestions”.
WindowsHelp
Article
.2007.Accessed01‐09‐2007
http://windowshelp.microsoft.com/Windows/en‐US/Help/afb7ed89‐ed63‐4e07‐
a482‐d7004a8f40121033.mspx
51. Microsoft,“WindowsServer2003CanTakeYouBackInTime”.
MSDNBlogEntry.
September2005.Accessed01‐09‐2007
http://blogs.msdn.com/oldnewthing/archive/2005/09/06/461390.aspx
52. Microsoft,“HowVolumeShadowCopyServiceWorks”.
MicrosoftTechNetArticle
.
March2003.Accessed01‐09‐2007
http://technet2.microsoft.com/WindowsServer/en/Library/2b0d2457‐b7d8‐
42c3‐b6c9‐59c145b7765f1033.mspx
53. Microsoft,“WhyDoRestorePointsInVistaUseSoMuchDiskSpace?”.
Microsoft
FilingCabinetBlog
.March2007.Accessed01‐09‐2007
http://blogs.technet.com/filecab/archive/2007/03/03/why‐do‐restore‐points‐in‐
windows‐vista‐use‐so‐much‐disk‐space.aspx

‐75‐
54. MichaelA.Penhallurick,“MethodologiesfortheUseofVMwaretoBoot
Cloned/MountedSubjectHardDiskImages”.March2005.Accessed01‐09‐2007
http://www.e5hforensics.com/Downloads/VMware%20Forensic%20Cloning%20
Methodology.pdf
55. DaveMethvin,“TheVistaBackupsThatYouCan’tHave”.
PCPitstopTechArticle
.
April2007.Accessed01‐09‐2007
http://pcpitstop.com/news/dave/2007‐04.asp
56. Software:“SDeletev1.51”.MarkRussinovich.November2006.Accessed01‐09‐
2007
http://www.microsoft.com/technet/sysinternals/Security/SDelete.mspx
57. Software:“Eraserv5.82”.G.TrantandS.Tolvanen.July2007.Accessed01‐09‐
2007
http://sourceforge.net/projects/eraser/
58. PeterGutmann,“SecureDeletionofDatafromMagneticandSolid‐StateMemory”.
6
th
USENIXSecuritySymposiumProceedings
.July1996.Accessed01‐09‐2007
http://www.cs.auckland.ac.nz/~pgut001/pubs/secure_del.html
59. Microsoft,“Vssadmin”.
MicrosoftTechNetArticle
.January2005.Accessed01‐09‐
2007
http://technet2.microsoft.com/windowsserver/en/library/89d2e411‐6977‐4808‐
9ad5‐476c9eaecaa51033.mspx?mfrtrue
60. Microsoft,“HowtoCreateaVirtualPCHardDiskImagebyUsingaBackupDisk
ImageFile”.March2007.Accessed01‐09‐2007
http://support.microsoft.com/kb/912826/en‐us
61. Microsoft,“NewHandlingforAccountData”.
MSDNDeveloperArticle
.Accessed01‐
09‐2007
http://msdn2.microsoft.com/en‐us/library/ms715237.aspx

‐76‐
62. WilliamStanek,“WindowsVista:TheDefinitiveGuide”.
O’ReillyMediaInc
.February
2007.
63. Microsoft,“UsingDigitalIDstoSignorEncryptWindowsMailMessages”.
Microsoft
WindowsVistaHelpArticle
.Accessed01‐09‐2007
http://windowshelp.microsoft.com/Windows/en‐US/Help/66a5a63f‐1d72‐4594‐
96da‐78d57f04852a1033.mspx
64. Microsoft,“WindowsContactSchemaOverview”.
MSDNDeveloperArticle
.
Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/ms735869.aspx
65. Microsoft,“AnnouncingIE7”.
MicrosoftMSDNDeveloperBlog
.May2006.
Accessed01‐09‐2007
http://blogs.msdn.com/ie/archive/2006/05/26/608255.aspx
66. Microsoft,“SecurityImprovementsinInternetExplorerforWindowsVista”.
MicrosoftVistaTechNetArticle
.Accessed01‐09‐2007
http://technet2.microsoft.com/WindowsVista/en/library/dfc3160b‐0578‐427d‐
8a48‐6b63a8e917b81033.mspx?mfrtrue
67. Microsoft,“SecurableObjects”.
MSDNDeveloperArticle
.February2007.Accessed
01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/aa379557.aspx
68. MikeFriedmanIE7SecurityTeam,“ProtectedModeinVistaIE7”.
MicrosoftMSDN
Blog.
February2006.Accessed01‐09‐2007
http://blogs.msdn.com/ie/archive/2006/02/09/528963.aspx
69. MarcSibleyandPeterBrundrett,“UnderstandingandWorkinginProtectedMode
InternetExplorer”.
MSDNDeveloperArticle.
January2006.Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/bb250462.aspx
70. AriPernickWindowsNetworkingTeam,“ABitaboutWinInet’sIndex.dat”.
MicrosoftMSDNBlog.
August2006.Accessed01‐09‐2007
http://blogs.msdn.com/wndp/archive/2006/08/04/WinInet‐Index‐dat.aspx

‐77‐
71. Microsoft,“userDataBehaviour”.Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/ms531424.aspx
72. PasscapeSoftware,“RecoveringInternetExplorerPasswords:TheoryandPractice”.
Accessed01‐09‐2007
http://www.passcape.com/internet_explorer_passwords.htm
73. Microsoft,“Pstore”.
MSDNDeveloperArticle
.June2007.Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/bb432403.aspx
74. J.MulliganandA.J.Elbirt.“DesktopSecurityandUsabilityTrade‐Offs:AnEvaluation
ofPasswordManagementSystems”.
InformationSystemsSecurity,Volume14Issue
2
.May01,2005.Accessed01‐09‐2007
http://www.libdirectory.idsc.gov.eg/cas/articles/computer&internet/computer2.
pdf
75. MikhaelFelker,“PasswordManagementConcernswithIEandFirefox,partone”.
SecurityFocusArticle.
August2006.Accessed01‐09‐2007
http://www.securityfocus.com/infocus/1882/2
76. Microsoft,“WindowsDataProtection”.
MSDNDeveloperArticle
.October2001.
Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/ms995355.aspx
77. Software:“PasscapeInternetExplorerPasswordRecoverybeta7v2.4.0.237”.
PasscapeSoftware.Accessed01‐09‐2007
http://www.passcape.com/internet_explorer_password_recovery.htm
78. KeithJ.Jones,“ForensicAnalysisofMicrosoftWindowsRecycleBinRecords”.
January2003.Accessed01‐09‐2007
http://www.e‐fense.com/helix/Docs/Recycler_Bin_Record_Reconstruction.pdf
79. GeorgeM.GarnerJr.,“ForensicAcquisitionUtilities”.August2007.Accessed01‐09‐
2007
http://www.gmgsystemsinc.com/fau/
80. Microsoft,“Device\PhysicalMemoryObject”.
MicrosoftTechNetArticle
.Accessed
01‐09‐2007

‐78‐
http://technet2.microsoft.com/windowsserver/en/library/e0f862a3‐cf16‐4a48‐
bea5‐f2004d12ce351033.mspx?mfrtrue
81. M.Becher,M.Dornseif,C.Klein,“FireWire–AllYourMemoryAreBelongToUs”.
CanSecWestConference2005
.Accessed01‐09‐2007
http://www.cansecwest.com/core05/2005‐firewire‐cansecwest.pdf
82. StephenD.Wolthusen,“WindowsDeviceInterfaceSecurity”.
InformationSecurity
TechnicalReport112006pp.160‐165
.Accessed01‐09‐2007
http://www.wolthusen.com/publications/ISTR2006.pdf
83. Microsoft,“KernelTransactionManager”.
MicrosoftMSDNArticle
.February2007.
Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/aa366295.aspx
84. Microsoft,“HowtoUseTransactionalNTFS”.
MicrosoftMSDNArticle
.February
2007.Accessed01‐09‐2007
http://msdn2.microsoft.com/en‐us/library/aa365008.aspx
85. Microsoft,“ShadowCopiesMayBeLostWhenYouDefragmentaVolume”.
Microsoft
KBArticle
.March2007.Accessed01‐09‐2007
http://support.microsoft.com/kb/312067
86. Microsoft,“DiskDefragmenterFAQ”.
MicrosoftFilingCabinetBlog
.April2007.
Accessed01‐09‐2007
http://blogs.technet.com/filecab/pages/disk‐defragmenter‐faq.aspx
87. Microsoft,“WindowsVistaProductGuide”.2006.Accessed01‐09‐2007
http://www.microsoft.com/downloads/details.aspx?FamilyIDbbc16ebf‐4823‐
4a12‐afe1‐5b40b2ad3725&displaylangen
88. AccessData,“RegistryQuickFindChart”.2005.Accessed01‐09‐2007
http://www.accessdata.com/media/en_US/print/papers/wp.Registry_Quick_Find_
Chart.en_us.pdf

‐79‐
89. Microsoft,“WindowsRegistryInformationforAdvancedUsers”.August2007.
Accessed01‐09‐2007
http://support.microsoft.com/kb/256986/

‐80‐
Appendix B
Features Comparison
Thissectionshowsatablewhichdocumentsthefeaturesavailable in each edition of
WindowsVistaTablereproducedfrom87.
Home
Basic
Home
Premium
Business
Enterprise
Ultimate
Key Features for All Users
WelcomeCenter Yes Yes Yes Yes Yes
UserAccountControl Yes Yes Yes Yes Yes
WindowsSecurityCenter Yes Yes Yes Yes Yes
WindowsDefender Yes Yes Yes Yes Yes
WindowsFirewall Yes Yes Yes Yes Yes
InternetExplorer7ProtectedMode Yes Yes Yes Yes Yes
InternetExplorer7FixMySettings Yes Yes Yes Yes Yes
Anti‐phishinginInternetExplorer7 Yes Yes Yes Yes Yes
Anti‐phishinginWindowsMail Yes Yes Yes Yes Yes
WindowsUpdate Yes Yes Yes Yes Yes
ServiceHardening Yes Yes Yes Yes Yes
Performanceself‐tuningandhardwarediagnostics Yes Yes Yes Yes Yes
WindowsExperienceIndex Yes Yes Yes Yes Yes
Next‐generationTCP/IPstack Yes Yes Yes Yes Yes
IPv6andIPv4support Yes Yes Yes Yes Yes
WindowsReadyDrive Yes Yes Yes Yes Yes
WindowsDisplayDriverModel(WDDM) Yes Yes Yes Yes Yes
Adhocbackupandrecoveryofuserfilesandfolders Yes Yes Yes Yes Yes
Scheduledbackupofuserfiles Yes Yes Yes Yes
BackupofuserfilestoanetworkedPCordevice Yes Yes Yes Yes

‐81‐
Home
Basic
Home
Premium
Business
Enterprise
Ultimate
Incrementalbackup Yes Yes Yes Yes
Automaticbackupscheduling Yes Yes Yes Yes
CompletePCBackupandRestore(imagebased) Yes Yes Yes
ShadowCopy(restorepreviousversionsofyour
documents)
Yes Yes Yes
WindowsVistaBasicuserinterface Yes Yes Yes Yes Yes
WindowsAerouserexperience(glass,dynamic
windows,andasmoother‐performingdesktop)
Yes Yes Yes Yes
InstantSearch Yes Yes Yes Yes Yes
Filetagging Yes Yes Yes Yes Yes
StackingandGroupByView. Yes Yes Yes Yes Yes
InternetExplorer7withRSSfeedsupport,tabbed
browsing,andintegratedsearch
Yes Yes Yes Yes Yes
.NETFramework3.0 Yes Yes Yes Yes Yes
WindowsCardSpace Yes Yes Yes Yes Yes
WindowsSuperFetch Yes Yes Yes Yes Yes
WindowsReadyBoost Yes Yes Yes Yes Yes
I/Oprioritization Yes Yes Yes Yes Yes
Automaticharddiskdefragmentation Yes Yes Yes Yes Yes
64‐bitprocessorsupport Yes Yes Yes Yes Yes
MaximumRAMsupportedwith32‐bitsystem 4GB 4GB 4GB 4GB 4GB
MaximumRAMsupportedwith64‐bitsystem 8GB 16GB 128+GB 128+GB 128+GB
Twoprocessors(twoprocessorsockets)support Yes Yes Yes
Yearsofproductsupport 5 5 10 10 5
Key Features for Home Users
WindowsMail Yes Yes Yes Yes Yes
WindowsCalendar Yes Yes Yes Yes Yes
WindowsSidebar Yes Yes Yes Yes Yes
WindowsPhotoGallery—fororganizing,editing,
printing,andsharingphotosandvideos
Yes Yes Yes Yes Yes

‐82‐
Home
Basic
Home
Premium
Business
Enterprise
Ultimate
Themedslideshows Yes Yes
WindowsMediaPlayer11 Yes Yes Yes Yes Yes
NativeDVDplayback Yes Yes
WindowsMediaCenter—formusic,photos,videos,
liveandrecordedTV,andonlineentertainment
Yes Yes
WindowsMediaCenter—forrecordingandwatching
high‐definitionTV(U.S.andSouthKoreaonly)
Yes Yes
WindowsMediaCenter—CableCardsupport(U.S.
only)
Yes Yes
SupportforMediaCenterExtenders,includingXbox
360
Yes Yes
WindowsMovieMaker Yes Yes Yes Yes Yes
WindowsMovieMakerHD Yes Yes
WindowsDVDMaker(VideoDVDAuthoringand
Burning)
Yes Yes
GamesExplorer Yes Yes Yes Yes Yes
Updatedgames Yes Yes Yes Yes Yes
Newpremiumgames Yes Yes* Yes* Yes
ParentalControls Yes Yes Yes
Universalgamecontrollersupport Yes Yes Yes* Yes* Yes
SpeechRecognition Yes Yes Yes Yes Yes
AccessibilitySettingsandEaseofAccessCenter Yes Yes Yes Yes Yes
Key Features for Business Users
XPSDocumentsupport Yes Yes Yes Yes Yes
SmallBusinessResources Yes Yes* Yes
WindowsFaxandScan Yes Yes* Yes*
NetworkandSharingCenter Yes Yes Yes Yes Yes
NetworkDiagnosticsandtroubleshooting Yes Yes Yes Yes Yes
Improvedwirelessnetworking Yes Yes Yes Yes Yes
Wirelessnetworkprovisioning Yes Yes Yes

‐83‐
Home
Basic
Home
Premium
Business
Enterprise
Ultimate
Improvedpeernetworking Yes Yes Yes Yes Yes
ImprovedVPNsupport Yes Yes Yes Yes Yes
Improvedpowermanagement Yes Yes Yes Yes Yes
SimultaneousSMBpeernetworkconnections 5 10 10 10 10
WindowsHotStart Yes Yes Yes Yes Yes
WindowsMobilityCenter Partial Partial Yes Yes Yes
SyncCenter Yes Yes Yes Yes Yes
OfflineFoldersupport Yes Yes Yes
WindowsTabletPCwithintegratedpen/digitalink
input
Yes Yes Yes Yes
WindowsTabletPCtouchscreensupport Yes Yes Yes Yes
WindowsTabletPChandwritingrecognition
improvements
Yes Yes Yes Yes
WindowsTabletPCusabilityandnavigation
improvements
Yes Yes Yes Yes
WindowsSideShow Yes Yes Yes Yes
WindowsMeetingSpace Viewonly Yes Yes Yes Yes
Improvedfileandfoldersharing Yes Yes Yes Yes Yes
Adhocbackupandrecoveryofuserfilesandfolders Yes Yes Yes Yes Yes
Scheduledbackupofuserfiles Yes Yes Yes Yes
Backupofuserfilestoanetworkdevice Yes Yes Yes Yes
Key Features for IT Professionals
Systemimage–basedbackupandrecovery Yes Yes Yes
EncryptingFileSystem Yes Yes Yes
Desktopdeploymenttoolsformanagednetworks Yes Yes Yes
Policy‐basedqualityofservicefornetworking Yes Yes Yes
WindowsRightsManagementServices(RMS)Client Yes Yes Yes
Controloverinstallationofdevicedrivers Yes Yes Yes
NetworkAccessProtectionClientAgent Yes Yes Yes

‐84‐
Home
Basic
Home
Premium
Business
Enterprise
Ultimate
Pluggablelogonauthenticationarchitecture Yes Yes Yes Yes Yes
WindowsBitLockerDriveEncryption Yes Yes
Supportforsimultaneousinstallationofmultipleuser
interfacelanguages
Yes Yes
Allworldwideuserinterfacelanguages
(36languagestotal)available
Yes Yes
SubsystemforUNIX‐basedapplications Yes Yes
ApplicationCompatibilityfeatures Yes Yes Yes Yes Yes
File‐basedimageformat(WIM) Yes Yes Yes Yes Yes
Appendix C

‐85‐
Registry Keys
ThischapterprovidesthelocationsoftheregistryhivesinVista.Itthendetailsanumberof
registry keys which are of interest to an examiner. The lists are based on the “Registry
QuickFindChart”byAccessData88.EntriesinthelistwereexaminedinaVistasystem
andtocheckforanychanges.Otherregistryentriesdiscovered during the course of the
projectresearchhavealsobeenadded.
C.1 – Registry Hive Locations
Table C.1 shows a list of registry hives in Vista and the correspondingfilelocations.Full
detailsofeachhiveareavailablefrom89.Anumberofotherhivesarealsopresentona
defaultVistaconfiguration11butappeartoholdnomajorsignificance from an
investigative standpoint. Backups of the registry hives are now stored in
C:\Windows
\system32\config\RegBack.
RegistryHive Location
HKEY_LOCAL_MACHINE\SAM C:\Windows\system32\config\SAM
HKEY_LOCAL_MACHINE\SECURITY C:\Windows\system32\config\SECURITY
HKEY_LOCAL_MACHINE\SOFTWARE C:\Windows\system32\config\SOFTWARE
HKEY_LOCAL_MACHINE\SYSTEM C:\Windows\system32\config\SYSTEM
HKEY_USERS\.DEFAULT C:\Windows\system32\config\DEFAULT
HKEY_USERS\<user_SID> C:\Users\<username>\NTUSER.DAT
TableC.1‐RegistryHivesofInterest
C.2 – Internet Explorer
Information File Location Description

‐86‐
Information File Location Description
IE7AutoComplete
Passwords
NTUSER.DAT \Software\Microsoft\Internet
Explorer\IntelliForms\Storage2
Encryptedlistof
AutoComplete
passwordssee
SectionXX
IE7AutoComplete
Strings
NTUSER.DAT \Software\Microsoft\Internet
Explorer\IntelliForms\Storage1
Encryptedlistof
AutoCompletestrings
seeSectionXX
IEURLHistory–
DaysSaved
SOFTWARE \Software\Microsoft\Windows\
CurrentVersion\Internet
Settings\Url History -
DaysToKeep
Thenumberofdays
IE7storesvisited
URLs
DefaultDownload
Directory
NTUSER.DAT \Software\Microsoft\Internet
Explorer - Download Directory
Thedefaultdownload
directory
IE7Settings
NTUSER.DAT \Software\Microsoft\Internet
Explorer\Main
ListofsettingsforIE7
TableC.2‐InternetExplorerKeys
C.3 – System Information
Information File Location Description
ComputerName
SYSTEM \ControlSet###\Control\
ComputerName\ComputerName
Computernamefrom
systemproperties
CurrentControl
Set
SYSTEM \Select - Current
Identifiesthecurrent
controlset
EventLogs
SYSTEM \ControlSet###\Services\
Eventlog\
Identifiesthelocation
oftheeventlogs
InstallDate
SOFTWARE \Microsoft\Windows NT\
CurrentVersion
Liststhedatethe
operatingsystemwas
installed
ProductName
SOFTWARE \Microsoft\Windows NT\
CurrentVersion
Liststhenameofthe
operatingsystem

‐87‐
Information File Location Description
RegisteredOwner
SOFTWARE \Microsoft\Windows NT\
CurrentVersion
Identifiesthe
registeredowner
enteredduring
installationcanbe
modifiedlater
Registered
Organization
SOFTWARE \Microsoft\Windows NT\
CurrentVersion
Identifiesthe
registered
organizationentered
duringinstallation
canbemodified
later
SystemRoot
SOFTWARE \Microsoft\Windows NT\
CurrentVersion
Identifiesthesystem
directory
LastUserLogged
In
SOFTWARE \Microsoft\Windows\
CurrentVersion\Authentication\
LogonUI - LastLoggedOnUser
Liststhelastuserthat
loggedintothesystem
MountedDevices
SYSTEM \MountedDevices
Listscurrentandprior
mounteddevicesthat
useadriveletter
Pagefile
SYSTEM \ControlSet###\Control\Session
Manager\Memory Management
Containsthepagefile
settingssuchas
location,size,setto
wipeetc.
Run
SOFTWARE \Microsoft\Windows\
CurrentVersion\Run
Listsprogramsthat
runautomatically
whenthesystemboots
TimeZone
SYSTEM \ControlSet###\Control\
TimeZoneInformation
Identifiesthetime
zoneenteredduring
installationcanbe
modifiedlater
USBDevices
SYSTEM \ControlSet###\Enum\USBSTOR
Liststhesystem’sUSB
devices
TableC.3–SystemInformationKeys

‐88‐
C.4 – Network Information
Information File Location Description
LocalGroups
SAM \Domains\Builtin\Aliases\Names
Listslocalaccount
securityidentifiers
LocalUsers
SAM \Domains\Account\Users\Names
Listslocalaccount
securityidentifiers
Printers–
CurrentlyDefined
SYSTEM \ControlSet###\Control\Print\
Printers
Listsallprintersthat
areconfiguredonthe
currentsystem
Printer‐Default
NTUSER.DAT \Software\Microsoft\
Windows NT\CurrentVersion\
Windows - Device
Identifiesthecurrent
defaultprinter
Printer
Information
SYSTEM \ControlSet###\Control\Print\
Environments\WindowsNTx86\
Drivers\Version...
Containsinformation
aboutthecurrent
printer
ProfileList
SOFTWARE \Microsoft\Windows NT\
CurrentVersion\ProfileList
Containstheuser
securityidentifierfor
userswithaprofileon
thesystem
TCP/IPData
SYSTEM \ControlSet###\Services\TCPIP\
Parameters
Liststhecurrent
system’sdomainand
hostnamedata
TCP/IPSettingsof
aNetwork
Adapter
SYSTEM \ControlSet###\Services\TCPIP\
Parameters\Interfaces\
<ServiceName>
Liststhecurrent
system’sIPaddress
andgateway
information
TableC.4–NetworkInformationKeys
Note: For the last entry in the above table, <ServiceName> can be found by finding the
appropriate key for a network adapter in
HKLM\SOFTWARE\Microsoft\Windows NT\
CurrentVersion\NetworkCards\
andthencheckingtheServiceNamevaluefortheadapter.

‐89‐
C.5 – User Data
Information File Location Description
FileExtensions\
Program
Associations
NTUSER.DAT Software\Microsoft\Windows\
CurrentVersion\Explorer\
FileExts
Identifiesassociated
programswithfile
extensions
LastLogonTime
SAM \Domains\Account\Users\F Key
Bytes9–16storethe
lastlogontime
LastTime
Password
Changed
SAM \Domains\Account\Users\F Key
Bytes25‐32storethe
lasttimethepassword
waschanged
Account
Expiration
SAM \Domains\Account\Users\F Key
Bytes33‐40storethe
accountexpiration.If
notexpirationisset
0xFFFFFFFFwillbe
shown
LastFailedLogin
SAM \Domains\Account\Users\F Key
Bytes41‐48storethe
lastunsuccessfullogon
MRU–
OpenSaved
NTUSER.DAT \Software\Microsoft\Windows\
CurrentVersion\Explorer\
ComDlg32\OpenSavePidlMRU
Liststhefilenameand
pathofthemost
recentfilessavedor
copiedtoaspecific
locationinWindows
MRU–
RecentDocuments
NTUSER.DAT \Software\Microsoft\Windows\
CurrentVersion\Explorer\
RecentDocs
Identifiesrecently
openeddocuments
MRU–
RunMRU
NTUSER.DAT \Software\Microsoft\Windows\
CurrentVersion\Explorer\RunMRU
Liststhemostrecent
commandsenteredin
theWindowsRunbox
noteprograms
startedusingStart‐
StartSearchwillnot
appearinthiskey

‐90‐
Information File Location Description
Executed
Programs
NTUSER.DAT
\
Software\Microsoft\Windows\
CurrentVersion\Explorer\
UserAssist\{75048700-EF1F-
11D0-9888-006097DEACF9}\Count
Listofprograms
executedonthe
comptuer
TableC.5–UserDataKeys

‐91‐
Appendix D
The BitLocker Command Line Interface (CLI)
ThisappendixlistssomeusefulcommandswhenusingtheBitLockerCLI.
D.1 – Parameter List for BitLocker CLI
TheCLIforBitLockermustberunfromanadministrativecommandprompt:
1. NavigatetoStart‐AllPrograms‐Accessories.Right‐clickonthe“command
prompt”iconandselect“Runasadministrator”whenprompted.Press“continue”in
theUACpopupwindow.
2. Inthecommandprompt,navigateto
c:\windows\system32.
3. Runthecommand
cscript manage-bde.wsf
Runningthescriptwiththe/?parametershowsthefollowingoptions:
manage-bde[.wsf] -parameter [arguments]
Description:
Configures BitLocker Drive Encryption on disk volumes.
Parameter List:
-status Provides information about BitLocker-capable volumes.
-on Encrypts the volume and turns BitLocker protection on.
-off Decrypts the volume and turns BitLocker protection off.
-pause Pauses encryption or decryption.
-resume Resumes encryption or decryption.
-lock Prevents access to BitLocker-encrypted data.
-unlock Allows access to BitLocker-encrypted data.
-autounlock Manages automatic unlocking of data volumes.
-protectors Manages protection methods for the encryption key.
-tpm Configures the computer's Trusted Platform Module (TPM).
-ForceRecovery or -fr
Forces a BitLocker-protected OS to recover on restarts.
-ComputerName or -cn
Runs on another computer. Examples: "ComputerX", "127.0.0.1"
-? or /? Displays brief help. Example: "-ParameterSet -?"
-Help or -h Displays complete help. Example: "-ParameterSet -h"
Examples:
manage-bde -status
manage-bde -on C: -RecoveryPassword -RecoveryKey F:\
manage-bde -unlock E: -RecoveryKey F:\84E151C1...7A62067A512.bek

‐92‐
D.2 – Useful Commands
Themostusefulcommandstoanexaminerinvolvethestatus,protectors,andunlock
parameters.Theparameterstobepassedto
manage-bde.wsfareshowninTableD.1:
Parameter Description
–status
Providestheencryptionstatusofallvolumes.
–status <driveletter>:
Providestheencryptionstatusofaparticular
volume.Replace<driveletter>withtheletterof
thevolumetobequeried.
–protectors –get <driveletter>:
Showsthekeyprotectorsforaparticularvolume.
Replace<driveletter> withtheletterofthe
volumetobequeried.
–protectors –get <driveletter>: -sek
<savepath>
Showsthekeyprotectorsforaparticularvolume.
Replace<driveletter> withtheletterofthe
volumetobequeried.Replace<savepath>withthe
pathwherethefilesaretobesaved.Careshouldbe
takentomanuallynotethenumericalrecoverykey.
–protectors –get <driveletter>: -Type
RecoveryPassword > <filename>
Pipesacopyofthenumericalpasswordfora
particularvolumetoafile.Replace<driveletter>
withtheletterofthevolumetobequeried.Replace
<filename>withthepathandfilenameofwhere
theoutputistobesaved.
–unlock <driveletter>: -
RecoveryPassword <pass>
Unlocksavolumeusingthenumericalrecovery
password.Replace<driveletter>withtheletter
ofthevolumetobeunlocked.Replace<pass>with
the48‐digitnumericalpassword.Thepasswordcan
beenteredwithorwithoutdashes.
–unlock <driveletter>: -RecoveryKey
<file>
Unlocksavolumeusingarecoverykey.Replace
<driveletter> withtheletterofthevolumetobe
unlocked.Replace<file>withthefilename
includingfullpathoftherecoverykey.Thispart
shouldbeenclosedininvertedcommasifthereare
anyspacesinthepath/filename.
TableD.1–UsefulCommandsforBitLockerCLI
